
Successfully passing the CompTIA SY0-601 exam to obtain certification makes it easy for you to become a top talent.” CompTIA Security+ SY0-601 contains many latest technologies: monitor and protect hybrid environments, including cloud, mobile, and IoT; operate under the premise of understanding applicable laws and policies (including governance, risk and compliance principles); identify and analyze And respond to security incidents”
It is not a simple matter to obtain CompTIA Security+ SY0-601 certification: first, you need to pay the exam fee of 370 dollars, secondly, you need to learn a lot of professional knowledge for the exam, and finally, you need to take the exam. This kind of process does not guarantee that you will pass the exam. Every year, many people cannot pass the exam smoothly!
I’m not trying to discourage everyone’s confidence, I just say that the CompTIA Security+ SY0-601 exam is not easy!
So I share 13 valid CompTIA SY0-601 exam questions for free to help you improve your skills and exam experience!
All the exam questions I shared are the latest updates! All SY0-601 exam dumps come from Lead4pass.com!
Lead4pass will help you save a lot of money and help you pass the exam successfully for the first time! And we have the best exam credibility! You are not the first to need us!
Table Of Content:
- Download CompTIA SY0-601 exam pdf online
- CompTIA SY0-601 exam video from Youtube
- The latest updated CompTIA SY0-601 exam practice questions
- CompTIA SY0-601 Exam Certification Coupon Code 2021
CompTIA SY0-601 exam pdf online for free
Share the CompTIA SY0-601 Dumps PDF for free From Lead4pass SY0-601 Dumps part of the distraction collected on Google Drive shared by Lead4pass
https://drive.google.com/file/d/1hik3E7_GnCvwsunrbfLKirgdPQSK4Uib/
CompTIA Security+ SY0-601 exam practice question and answer online practice exam from Lead4pass
QUESTION 1
A Chief Executive Officer\\’s (CEO) personal information was stolen in a social engineering attack. Which of the
following sources would reveal if the CEO\\’s personal information is for sale?
A. Automated information sharing
B. Open-source intelligence
C. The dark web
D. Vulnerability databases
Correct Answer: C
QUESTION 2
A security analyst is performing a packet capture on a series of SOAP HTTP requests for a security assessment. The
analyst redirects the output to a file After the capture is complete, the analyst needs to review the first transactions
quickly and then search the entire series of requests for a particular string Which of the following would be BEST to use
to accomplish the task? (Select TWO).
A. head
B. Tcpdump
C. grep
D. rail
E. curl
F. openssi
G. dd
Correct Answer: AB
QUESTION 3
A company has determined that if its computer-based manufacturing is not functioning for 12 consecutive hours, it will
lose more money than it costs to maintain the equipment. Which of the following must be less than 12 hours to maintain
a positive total cost of ownership?
A. MTBF
B. RPO
C. RTO
D. MTTR
Correct Answer: C
QUESTION 4
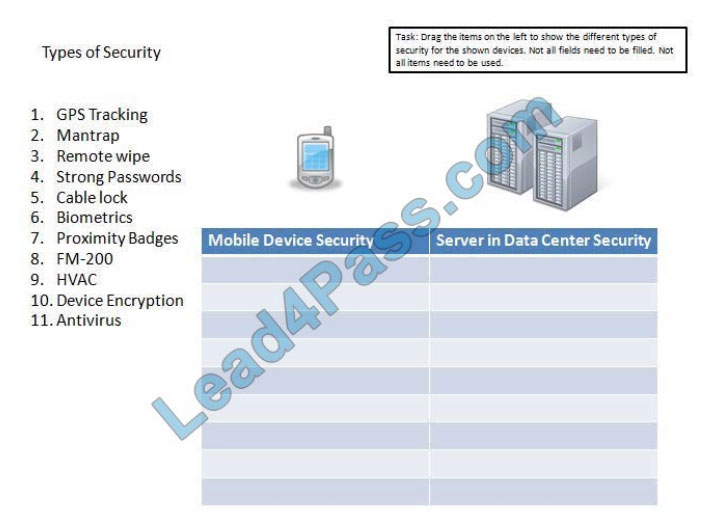
Drag the items on the left to show the different types of security for the shown devices. Not all fields need to be filled.
Not all items need to be used.
Select and Place:
Correct Answer:
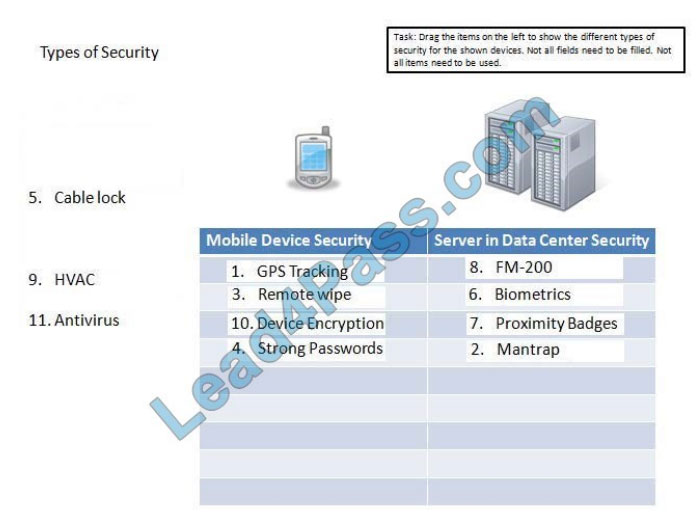
For mobile devices, at bare minimum, you should have the following security measures in place: Screen lock, Strong
password, Device encryption, Remote wipe/Sanitation, voice encryption, GPS tracking, Application control, Storage
segmentation, Asset tracking as well as Device Access control.
For servers in a data center your security should include: Fire extinguishers such as FM200 as part of fire suppression;
Biometric, proximity badges, mantraps, HVAC, cable locks;
these can all be physical security measures to control access to the server.
References:
Dulaney, Emmett and Chuck Easton, CompTIA Security+ Study Guide, 6th Edition, Sybex, Indianapolis, 2014, p. 418
QUESTION 5
A user contacts the help desk to report the following:
Two days ago, a pop-up browser window prompted the user for a name and password after connecting to the corporate wireless SSID. This had never happened before, but the user entered the information as requested. The user was able to access the Internet but had trouble accessing the department share until the next day.
The user is now getting notifications from the bank about unauthorized transactions.
Which of the following attack vectors was MOST likely used in this scenario?
A. Rogue access point
B. Evil twin
C. DNS poisoning
D. ARP poisoning
Correct Answer: A
QUESTION 6
A network administrator has been asked to design a solution to improve a company\\’s security posture The
administrator is given the following, requirements?
1. The solution must be inline in the network
2. The solution must be able to block known malicious traffic
3. The solution must be able to stop network-based attacks
Which of the following should the network administrator implement to BEST meet these requirements?
A. HIDS
B. NIDS
C. HIPS
D. NIPS
Correct Answer: D
QUESTION 7
A company provides mobile devices to its users to permit access to email and enterprise applications. The company
recently started allowing users to select from several different vendors and device models. When configuring the MDM,
which of the following is a key security implication of this heterogeneous device approach?
A. The most common set of MDM configurations will become the effective set of enterprise mobile security controls.
B. All devices will need to support SCEP-based enrollment; therefore, the heterogeneity of the chosen architecture may
unnecessarily expose private keys to adversaries.
C. Certain devices are inherently less secure than others, so compensatory controls will be needed to address the delta
between device vendors.
D. MDMs typically will not support heterogeneous deployment environments, so multiple MDMs will need to be installed
and configured.
Correct Answer: C
QUESTION 8
During an incident response, a security analyst observes the following log entry on the webserver:
Which of the following BEST describes the type of attack the analyst is experiencing?
A. SQL injection
B. Cross-site scripting
C. Pass-the-hash
D. Directory traversal
Correct Answer: B
QUESTION 9
An incident response technician collected a mobile device during an investigation. Which of the following should the
technician do maintain chain of custody?
A. Document the collection and require a sign-off when possession changes.
B. Lock the device in a safe or other secure location to prevent theft or alteration.
C. Place the device in a Faraday cage to prevent corruption of the data.
D. Record the collection in a blockchain-protected public ledger.
Correct Answer: A
QUESTION 10
Which of the following should be put in place when negotiating with a new vendor about the timeliness of the response to a significant outage or incident?
A. MOU
B. MTTR
C. SLA
D. NDA
Correct Answer: C
QUESTION 11
A retail executive recently accepted a job with a major competitor. The following week, a security analyst reviews the
security logs and identifies successful login attempts to access the departed executive\\’s accounts. Which of the
following security practices would have addressed the issue?
A. A non-disclosure agreement
B. Least privilege
C. An acceptable use policy
D. Ofboarding
Correct Answer: D
QUESTION 12
Which of the following control sets should a well-written BCP include? (Select THREE)
A. Preventive
B. Detective
C. Deterrent
D. Corrective
E. Compensating
F. Physical
G. Recovery
Correct Answer: ADG
QUESTION 13
An analyst needs to set up a method for securely transferring files between systems. One of the requirements is to
authenticate the IP header and the payload. Which of the following services would BEST meet the criteria?
A. TLS
B. PFS
C. ESP
D. AH
Correct Answer: A
Get the latest and complete CompTIA Security+ SY0-601 exam dumps! Help you pass the first exam successfully! Click here for more…
CompTIA Security+ SY0-601 Exam Certification Coupon Code 2021
You have read my entire article, and I have already told you how to successfully pass the CompTIA Security+ SY0-601 exam. You can choose: https://www.leads4pass.com/sy0-601.html and go directly to SY0-601 Exam dumps channel! Get your key to successfully pass the exam!
Wish you be happy!
ps.
Get free CompTIA SY0-601 dumps PDF online: https://drive.google.com/file/d/1hik3E7_GnCvwsunrbfLKirgdPQSK4Uib/

![[2021.3] lead4pass sy0-601 practice test q2](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-4.jpg)
![[2021.3] lead4pass sy0-601 practice test q2-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-1-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q2-2](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-2-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q9](https://www.braindump4it.com/wp-content/uploads/2021/03/q9.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-3](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-3.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-2](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-2.jpg)