
SecurityX, formerly CASP+, The name change emphasizes the advanced, or “Xpert” level certifications in the CompTIA portfolio. covers the technical knowledge and skills required to build, design, integrate and implement security solutions in complex environments.
Compared with the previous certification project, there is not much change. But starting from this year to participate in SecurityX certification, you need to look for the CAS-005 exam code.
When choosing the best resources to study for the new CompTIA SecurityX exam, you will definitely also want to know how many days it will take to really master all the exam content, let me tell you it will only take 3 days, it all depends on a few core factors explored in this article.
The Ultimate Guide to CompTIA SecurityX will also explore what you’ll be taking on the test, discuss the best ways to prepare for SecurityX, and answer your most common questions.
About CompTIA SecurityX
To prepare for the CompTIA SecurityX exam in 3 days, you first need to familiarize yourself with the Leads4Pass exam materials.
The CompTIA SecurityX exam is designed to test the advanced knowledge and skills of IT and security professionals. Here are some key aspects of the exam:
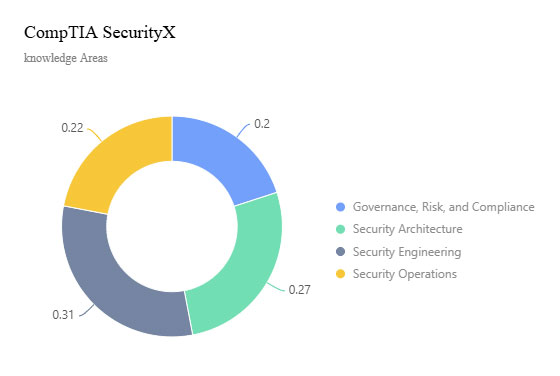
The CompTIA SecurityX exam covers 4 knowledge areas, including:
- Governance, Risk, and Compliance: Requires a comprehensive understanding of information security principles and their application in organizational contexts, with a particular focus on emerging challenges and considerations related to artificial intelligence
- Security Architecture: Assess your ability to design and implement secure and resilient systems, taking into account all aspects of security throughout the system lifecycle
- Security Engineering: Evaluate your ability to handle advanced security challenges, including troubleshooting, implementing security controls, and applying advanced security concepts in real-world scenarios.
- Security Operations: Assess your ability to leverage data and intelligence to proactively identify and respond to security threats and effectively investigate and respond to security incidents
Exam Format:
Question Types: The exam includes a combination of multiple-choice questions, drag-and-drop activities, and performance-based items.
Number of Questions: There are a maximum of 90 questions on the exam.
Time Limit: You have 165 minutes to complete the exam.
Passing Score: This test has no scaled score
CompTIA SecurityX does not require candidates to have formal prerequisites. but,It is recommended that candidates have at least 10 years of practical IT experience, of which 5 years are in security, with knowledge of Network+, Security+, CySA+, Cloud+ and PenTest+ or equivalent
Certification Roadmap
CompTIA SecurityX certification requires a solid foundation in cybersecurity concepts and extensive practical experience.
We think the CompTIA SecurityX certification will unlock your expert potential and take you to the next level by leveraging the comprehensive set of skills in the CompTIA Xpert series.
Prepare for the CompTIA SecurityX exam in 3 days
Why 3 days, this is a study plan!
According to the planned plan, you only need 3 days to prepare for CompTIA SecurityX learning!
Day one:
Download the 2025 CompTIA SecurityX CAS-005 exam simulation materials with 195 exam questions and answers in Leads4pass. You can choose PDF, VCE, or PDF+VCE learning tools. You can use PC or mobile phone to easily practice the test. The content covers the four core contents of CompTIA SecurityX that are real and effective.
If you use the VCE tool, first you can get familiar with using this tool. Then spend 2-3 hours reading all the exam questions and taking a practice test to find the current deficiencies, and then spend some time sorting out and understanding the wrong questions. Leads4Pass CAS -005 VCE simulation tool provides explanation and analysis of wrong questions to ensure that you can study efficiently.
Day two:
Build Confidence: You need to take the test again, and this time you need to take the questions you got wrong last time seriously and not only know how to do them but also truly understand what they mean. This step ensures that you can actually complete each question with ease in the actual exam. If there are still errors, they should be resolved and understood in time.
Day Three:
Consolidate your mentality: You should take at least 2 complete mock tests. This is very important! Complete exercises to ensure that you cannot miss any questions. This is an important step to ensure that you pass. Today you should take at least one mock test, and you need to ensure that you answer the questions with full marks, and then relax Mentality, take a good rest to ensure you are mentally prepared for the actual exam.
CompTIA SecurityX exam material display
| Free Download | source |
| CAS-005 PDF | Leads4Pass |
Question 1:
A security review revealed that not all of the client proxy traffic is being captured. Which of the following architectural changes best enables the capture of traffic for analysis?
A. Adding an additional proxy server to each segmented VLAN
B. Setting up a reverse proxy for client logging at the gateway
C. Configuring a span port on the perimeter firewall to ingest logs
D. Enabling client device logging and system event auditing
Correct Answer: C
Configuring a span port on the perimeter firewall to ingest logs is the best architectural change to ensure that all client proxy traffic is captured for analysis. Here\’s why:
Comprehensive Traffic Capture: A span port (or mirror port) on the perimeter firewall can capture all inbound and outbound traffic, including traffic that might bypass the proxy. This ensures that all network traffic is available for analysis.
Centralized Logging: By capturing logs at the perimeter firewall, the organization can centralize logging and analysis, making it easier to detect and investigate anomalies. Minimal Disruption: Implementing a span port is a non-intrusive
method that does not require significant changes to the network architecture, thus minimizing disruption to existing services.
Question 2:
A security architect is reviewing the following organizational specifications for a new application:
1.
Be sessionless and API-based
2.
Accept uploaded documents with PII, so all storage must be ephemeral
3.
Be able to scale on-demand across multiple nodes
4.
Restrict all network access except for the TLS port
Which of the following ways should the architect recommend the application be deployed in order to meet security and organizational infrastructure requirements?
A. Utilizing the cloud container service
B. On server instances with autoscaling groups
C. Using scripted delivery
D. With a content delivery network
Correct Answer: A
Deploying the application using a cloud container service aligns well with the specified security and organizational infrastructure requirements. It ensures sessionless, API-based operation, supports ephemeral storage for uploaded documents with PII, enables on-demand scalability across multiple nodes, and facilitates strict restriction of network access except for the TLS port.
Question 3:
A security analyst is participating in a risk assessment and is helping to calculate the exposure factor associated with various systems and processes within the organization. Which of the following resources would be most useful to calculate the exposure factor in this scenario?
A. Gap analysis
B. Business impact analysis
C. Risk register
D. Information security policy
E. Lessons learned
Correct Answer: B
Question 4:
A security engineer has learned that terminated employees\’ accounts are not being disabled. The termination dates are updated automatically in the human resources information system software by the appropriate human resources staff. Which of the following would best reduce risks to the organization?
A. Exporting reports from the system on a weekly basis to disable terminated employees\’ accounts
B. Granting permission to human resources staff to mark terminated employees\’ accounts as disabled
C. Configuring allowed login times for all staff to only work during business hours
D. Automating a process to disable the accounts by integrating Active Directory and human resources information systems
Correct Answer: D
Automating the process to disable terminated employees\’ accounts by integrating Active Directory (or any other authentication system) with the human resources information system (HRIS) is the best approach to reduce risks to the organization. By automating this process, the organization ensures that accounts are disabled promptly and consistently whenever an employee\’s termination date is updated in the HRIS. This reduces the window of opportunity for terminated employees to retain access to systems and sensitive information after leaving the organization.
Question 5:
An organization mat performs real-time financial processing is implementing a new backup solution Given the following business requirements?
1.
The backup solution must reduce the risk for potential backup compromise
2.
The backup solution must be resilient to a ransomware attack.
3.
The time to restore from backups is less important than the backup data integrity
4.
Multiple copies of production data must be maintained
Which of the following backup strategies best meets these requirement?
A. Creating a secondary, immutable storage array and updating it with live data on a continuous basis
B. Utilizing two connected storage arrays and ensuring the arrays constantly sync
C. Enabling remote journaling on the databases to ensure real-time transactions are mirrored
D. Setting up antitempering on the databases to ensure data cannot be changed unintentionally
Correct Answer: A
A. Creating a secondary, immutable storage array and updating it with live data on a continuous basis: An immutable storage array ensures that data, once written, cannot be altered or deleted. This greatly reduces the risk of backup
compromise and provides resilience against ransomware attacks, as the ransomware cannot modify or delete the backup data. Maintaining multiple copies of production data with an immutable storage solution ensures data integrity and
compliance with the requirement for multiple copies.
Other options:
B. Utilizing two connected storage arrays and ensuring the arrays constantly sync:
While this ensures data redundancy, it does not provide protection against ransomware attacks, as both arrays could be compromised simultaneously. C. Enabling remote journaling on the databases: This ensures real-time transaction
mirroring but does not address the requirement for reducing the risk of backup compromise or resilience to ransomware.
D. Setting up anti-tampering on the databases: While this helps ensure data integrity, it does not provide a comprehensive backup solution that meets all the specified requirements.
References:
CompTIA Security+ Study Guide
NIST SP 800-209, “Security Guidelines for Storage Infrastructure” “Immutable Backup Architecture” by Veeam
Question 6:
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent
Which of the following actions should the company lake to most likely improve the vulnerability management process\’
A. Request a weekly report with all new assets deployed and decommissioned
B. Extend the DHCP lease lime to allow the devices to remain with the same address for a longer period.
C. Implement a shadow IT detection process to avoid rogue devices on the network
D. Perform regular discovery scanning throughout the 11 landscape using the vulnerability management tool
Correct Answer: D
To improve the vulnerability management process in an environment where new devices/IPs are added and dropped regularly, the company should perform regular discovery scanning throughout the IT landscape using the vulnerability management tool.
Here\’s why:
Accurate Asset Inventory: Regular discovery scans help maintain an up-to-date inventory of all assets, ensuring that the vulnerability management process includes all relevant devices and IPs. Consistency in Reporting: By continuously
discovering and scanning new and existing assets, the company can generate consistent and comprehensive vulnerability reports that reflect the current state of the network. Proactive Management:
Regular scans enable the organization to proactively identify and address vulnerabilities on new and existing assets, reducing the window of exposure to potential threats.
Question 7:
A company recently deployed new servers to create an additional cluster to support a new application. The corporate security policy states that all new servers must be resilient. The new cluster has a high- availability configuration for a smooth failover. The failover was successful following a recent power outage, but both clusters lost critical data, which impacted recovery time. Which of the following needs to be configured to help ensure minimal delays when power outages occur in the future?
A. Replication
B. Caching
C. Containerization
D. Redundancy
E. High availability
Correct Answer: A
Based on the requirement to reduce delays during power outages and the scenario\’s description of data loss despite high availability, configuring replication (option A) is crucial. Replication ensures that critical data is duplicated across clusters, allowing seamless failover and access to data from alternative locations in the event of server failures or power outages. This approach directly addresses the need for data resilience and continuity, ensuring minimal impact on operations during unforeseen disruptions. Thus, replication is the most suitable solution to enhance the company\’s data resilience and reduce recovery times during power outages.
Question 8:
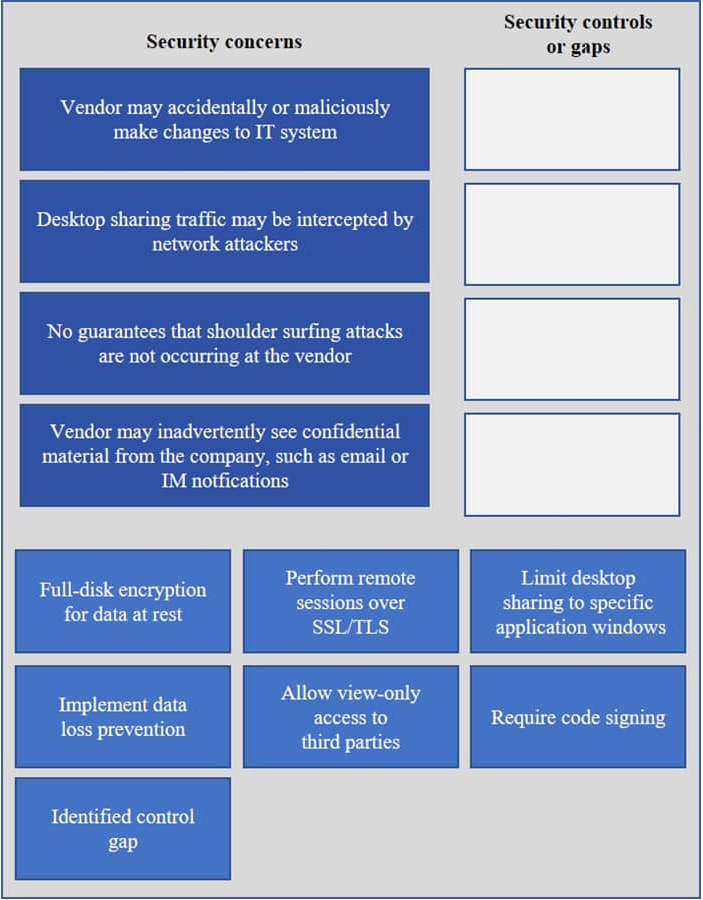
DRAG DROP
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern.
Options may be used once or not at all.
Select and Place:
Correct Answer:
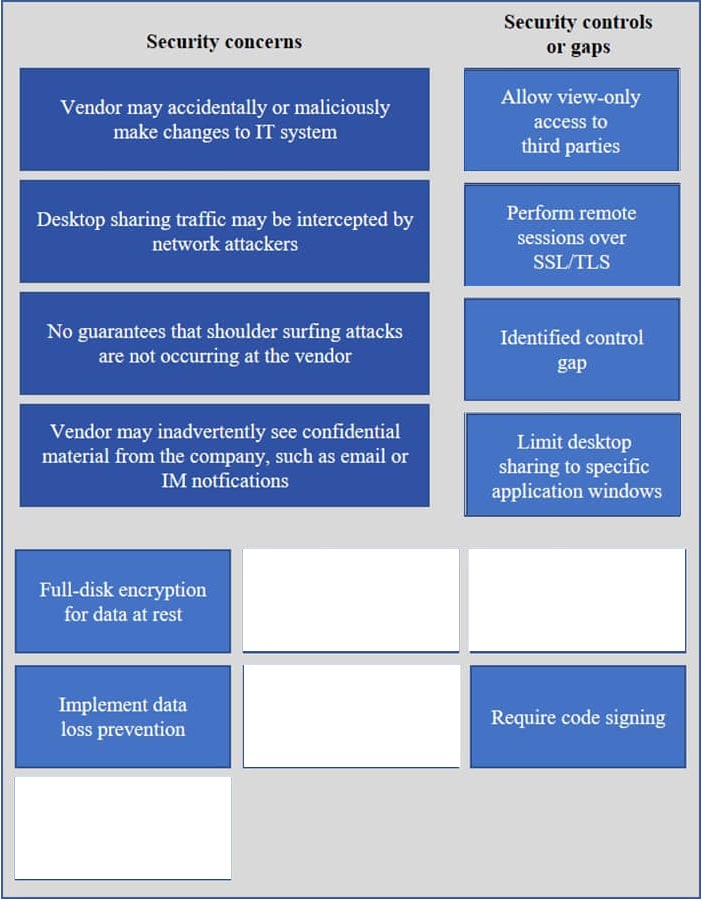
Vendor may accidentally or maliciously make changes to the IT system – Allow view-only access.
With view-only access, the third party can view the desktop but cannot interact with it. In other words, they cannot control the keyboard or mouse to make any changes.
Desktop sharing traffic may be intercepted by network attackers – Use SSL for remote sessions.
SSL (Secure Sockets Layer) encrypts data in transit between computers. If an attacker intercepted the traffic, the data would be encrypted and therefore unreadable to the attacker.
No guarantees that shoulder surfing attacks are not occurring at the vendor – Identified control gap.
Shoulder surfing is where someone else gains information by looking at your computer screen. This should be identified as a risk. A control gap occurs when there are either insufficient or no actions taken to avoid or mitigate a significant risk.
Vendor may inadvertently see confidential material from the company such as email and IMs – Limit desktop session to certain windows.
The easiest way to prevent a third party from viewing your emails and IMs is to close the email and IM application windows for the duration of the desktop sharing session.
Question 9:
An organization is developing on Al-enabled digital worker to help employees complete common tasks such as template development, editing, research, and scheduling. As part of the Al workload the organization wants to Implement guardrails within the platform.
Which of the following should the company do to secure the Al environment?
A. Limn the platform\’s abilities to only non-sensitive functions
B. Enhance the training model\’s effectiveness.
C. Grant the system the ability to self-govern
D. Require end-user acknowledgement of organizational policies.
Correct Answer: A
Limiting the platform\’s abilities to only non-sensitive functions helps to mitigate risks associated with AI operations. By ensuring that the AI-enabled digital worker is only allowed to perform tasks that do not involve sensitive or critical data, the
organization reduces the potential impact of any security breaches or misuse. Enhancing the training model\’s effectiveness (Option B) is important but does not directly address security guardrails. Granting the system the ability to self-govern
(Option C) could increase risk as it may act beyond the organization\’s control. Requiring end-user acknowledgement of organizational policies (Option D) is a good practice but does not implement technical guardrails to secure the AI environment.
References:
CompTIA Security+ Study Guide
NIST SP 800-53 Rev. 5, “Security and Privacy Controls for Information Systems and Organizations”
ISO/IEC 27001, “Information Security Management”
Question 10:
A security engineer performed a code scan that resulted in many false positives. The security engineer must find a solution that improves the quality of scanning results before application deployment.
Which of the following is the best solution?
A. Limiting the tool to a specific coding language and tuning the rule set
B. Configuring branch protection rules and dependency checks
C. Using an application vulnerability scanner to identify coding flaws in production
D. Performing updates on code libraries before code development
Correct Answer: A
To improve the quality of code scanning results and reduce false positives, the best solution is to limit the tool to a specific coding language and fine-tune the rule set. By configuring the code scanning tool to focus on the specific language
used in the application, the tool can more accurately identify relevant issues and reduce the number of false positives. Additionally, tuning the rule set ensures that the tool\’s checks are appropriate for the application\’s context, further improving the accuracy of the scan results.
References:
CompTIA SecurityX Study Guide: Discusses best practices for configuring code scanning tools, including language-specific tuning and rule set adjustments. “Secure Coding: Principles and Practices” by Mark G. Graff and Kenneth R. van
Wyk: Highlights the importance of customizing code analysis tools to reduce false positives.
OWASP (Open Web Application Security Project): Provides guidelines for configuring and tuning code scanning tools to improve accuracy.
Question 11:
DRAG DROP
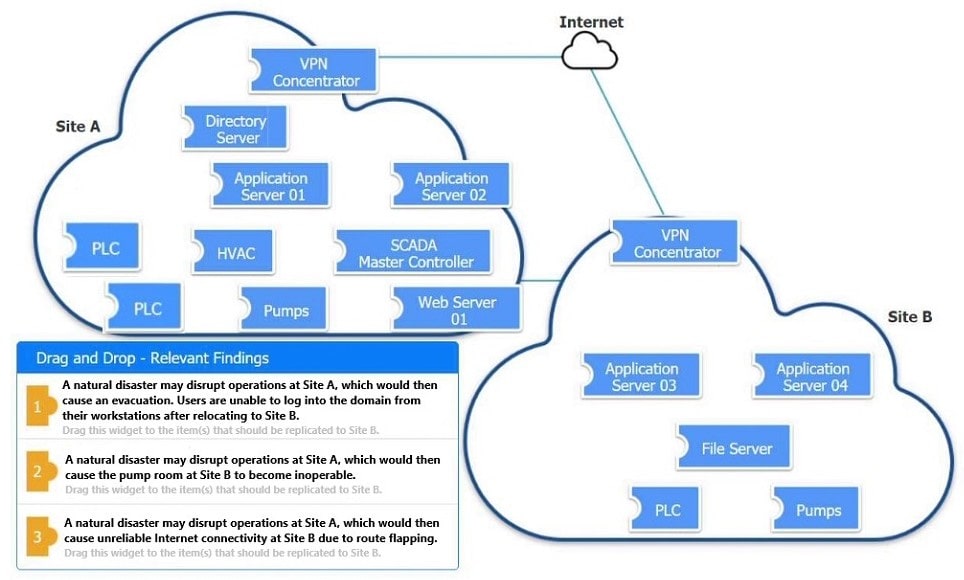
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
Select and Place:
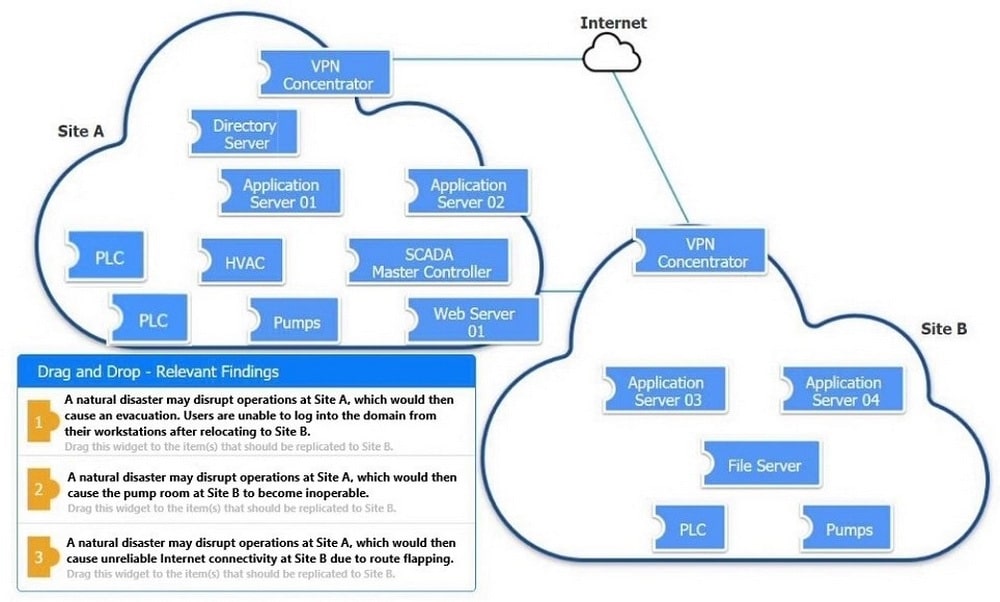
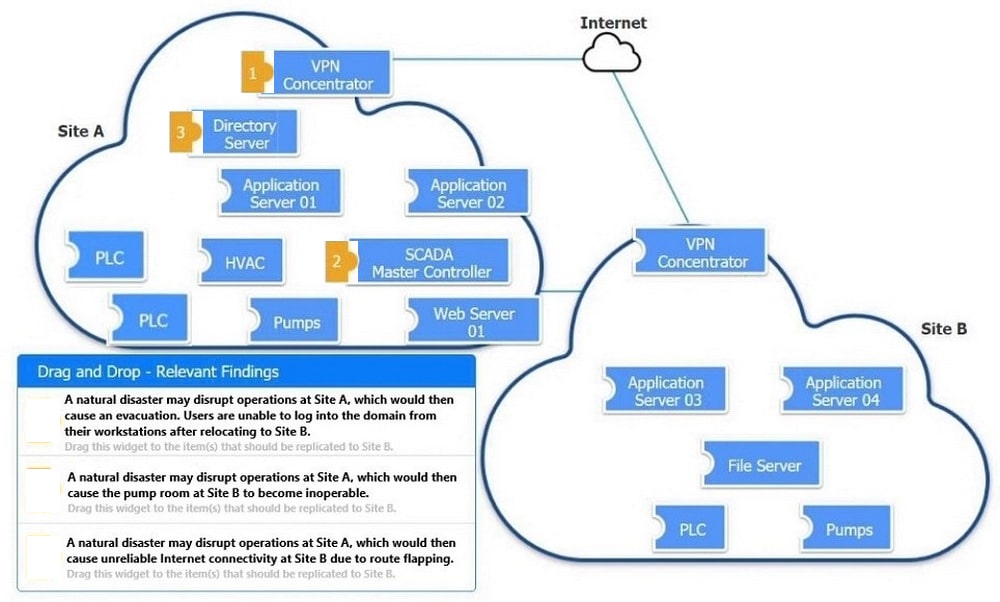
Correct Answer:
Question 12:
A junior security researcher has identified a buffer overflow vulnerability leading to remote code execution in a former employer\’s software. The security researcher asks for the manager\’s advice on the vulnerability submission process. Which of the following is the best advice the current manager can provide the security researcher?
A. Collect proof that the exploit works in order to expedite the process.
B. Publish proof-of-concept exploit code on a personal blog.
C. Recommend legal consultation about the process.
D. Visit a bug bounty website for the latest information.
Correct Answer: C
Legal consultation is crucial before proceeding with any vulnerability disclosure process, especially when dealing with vulnerabilities found in former employers\’ software. It ensures that the researcher adheres to legal and ethical standards, protects their rights, and avoids potential legal risks associated with disclosure. Therefore, advising the security researcher to seek legal consultation is the most prudent course of action in this situation.
Question 13:
Users are experiencing a variety of issues when trying to access corporate resources examples include
1.
Connectivity issues between local computers and file servers within branch offices
2.
Inability to download corporate applications on mobile endpoints wtiilc working remotely
3.
Certificate errors when accessing internal web applications
Which of the following actions are the most relevant when troubleshooting the reported issues? (Select two).
A. Review VPN throughput
B. Check IPS rules
C. Restore static content on lite CDN.
D. Enable secure authentication using NAC
E. Implement advanced WAF rules.
F. Validate MDM asset compliance
Correct Answer: AF
The reported issues suggest problems related to network connectivity, remote access, and certificate management:
A. Review VPN throughput: Connectivity issues and the inability to download applications while working remotely may be due to VPN bandwidth or performance issues. Reviewing and optimizing VPN throughput can help resolve these
problems by ensuring that remote users have adequate bandwidth for accessing corporate resources.
F. Validate MDM asset compliance: Mobile Device Management (MDM) systems ensure that mobile endpoints comply with corporate security policies. Validating MDM compliance can help address issues related to the inability to download
applications and certificate errors, as non-compliant devices might be blocked from accessing certain resources.
B. Check IPS rules: While important for security, IPS rules are less likely to directly address the connectivity and certificate issues described. C. Restore static content on the CDN: This action is related to content delivery but does not address
VPN or certificate-related issues. D. Enable secure authentication using NAC: Network Access Control (NAC) enhances security but does not directly address the specific issues described. E. Implement advanced WAF rules: Web Application
Firewalls protect web applications but do not address VPN throughput or mobile device compliance.
References:
CompTIA Security+ Study Guide
NIST SP 800-77, “Guide to IPsec VPNs”
CIS Controls, “Control 11: Secure Configuration for Network Devices”
Question 14:
Which of the following provides the best solution for organizations that want to securely back up the MFA seeds for its employees in a central, offline location with minimal management overhead?
A. Key escrow service
B. Secrets management
C. Encrypted database
D. Hardware security module
Correct Answer: D
An HSM provides a highly secure method for storing and managing cryptographic keys and other sensitive data, including MFA seeds. HSMs are designed to be tamper-resistant and are capable of securely generating, storing, and backing up cryptographic keys in an offline environment. Once configured, HSMs require minimal management overhead and provide robust security features, including physical security, to protect the stored data.
Question 15:
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function:
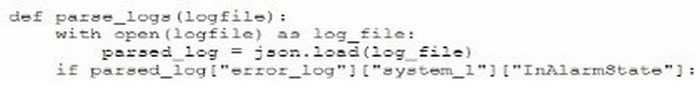
Which of the following is most likely the log input that the code will parse?
A. [“error_log] [“system_1”] [“InAlarmState”: True]
B. <“error_log”><“system_1”>
C. error_log;
-system_1:
InAlarmState: True
D. {“error_log”: {“system_1”: {“InAlarmState”: True}}}
Correct Answer: A
…
You can also download the CompTIA SecurityX CAS-005 PDF practice test
Conclusion
CompTIA SecurityX is a cybersecurity certification worth pursuing.
But it is a more difficult certification and not easy to obtain. Obtaining the CompTIA SecurityX certification requires using useful learning resources and following a reasonable plan to complete the goals, such as the 3-day learning plan I recommend.
You can join the Leads4Pass scheme to access over 1,000 courses and VCE practice tests to help you prepare for your upcoming exams.
FAQ
Is the CompTIA SecurityX exam difficult?
Yes it is more difficult! More than just a CASP+ exam, CompTIA SecurityX highlights advanced or “Xpert” level certifications within the CompTIA portfolio.
Can I get a job with CompTIA SecurityX 2025?
Of course, this is an advanced certification! The upgraded CASP+ meets the current needs of AI, is very suitable for future development, and has a variety of job types suitable for you, such as: Security Architect, Cybersecurity Engineer, SOC Manager, Cyber Risk Analyst, Chief Information Security Officer
What is the salary situation at CompTIA SecurityX?
This has a lot to do with the position you choose and your work experience.
CompTIA salaries increase every year based on your work experience, and the CompTIA Xpert series of certifications are for IT professionals with years of experience who want to validate their expert-level knowledge of business-critical technologies. Therefore, obtaining CompTIA SecurityX certification will definitely earn you a lot of money.