
SY0-601 dumps have been updated to prepare for the CompTIA Security+ certification exam.
Prepare for the CompTIA Security+ 2022 certification exam Choose Lead4Pass, a reliable IT certification provider, you just need to download the SY0-601 dumps from https://www.leads4pass.com/sy0-601.html, guaranteeing you a successful first attempt to pass the target exam.
Because Lead4Pass sy0-601 dumps have a long-term good reputation from 2016 to now, it can help candidates truly pass the CompTIA Security+ 2022 certification exam. So you just need to practice sy0-601 dumps to ensure that you pass the CompTIA Security+ 2022 certification exam 100%.
You can also practice some sy0-601 dumps questions online first:
Answers are announced at the end of the article
QUESTION 1:
A security analyst is performing a packet capture on a series of SOAP HTTP requests for a security assessment. The analyst redirects the output to a file After the capture is complete, the analyst needs to review the first transactions quickly and then search the entire series of requests for a particular string Which of the following would be the BEST to use to accomplish the task? (Select TWO).
A. head
B. Tcpdump
C. grep
D. rail
E. curl
F. openssi
G. dd
QUESTION 2:
The facilities supervisor for a government agency is concerned about unauthorized access to environmental systems in the event the staff WiFi network is breached. Which of the blowing would BEST address this security concern?
A. install a smart meter on the staff WiFi.
B. Place the environmental systems in the same DHCP scope as the staff WiFi.
C. Implement Zigbee on the staff WiFi access points.
D. Segment the staff WiFi network from the environmental system’s network.
QUESTION 3:
Users at organizations have been installing programs from the internet on their workstations without first proper authorization. The organization maintains a portal from which users can install standardized programs. However, some users have administrative access to their workstations to enable legacy programs to function properly. Which of the following should the security administrator consider implementing to address this issue?
A. Application code signing
B. Application whitelisting
C. Data loss prevention
D. Web application firewalls
QUESTION 4:
A software developer needs to perform code-execution testing, black-box testing, and non-functional testing on a new product before its general release. Which of the following BEST describes the tasks the developer is conducting?
A. Verification
B. Validation
C. Normalization
D. Staging
QUESTION 5:
A security analyst needs to perform periodic vulnerability scans on production systems. Which of the following scan Types would produce the BEST vulnerability scan report?
A. Port
B. Intrusive
C. Host discovery
D. Credentialed
QUESTION 6:
A cybersecurity analyst needs to implement secure authentication to third-party websites without users\’ passwords.
Which of the following would be the BEST way to achieve this objective?
A. OAuth
B. SSO
C. SAML
D. PAP
QUESTION 7:
A company is required to continue using legacy software to support a critical service. Which of the following BEST explains a risk of this practice?
A. Default system configuration
B. Unsecure protocols
C. Lack of vendor support
D. Weak encryption
QUESTION 8:
A company has discovered unauthorized devices are using its WiFi network, and it wants to harden the access point to improve security.
Which of the following configuration should an analyst enable to improve security? (Select Two)
A. RADIUS
B. PEAP
C. WPS
D. WEP-TKIP
E. SSL
F. WPA2-PSK
QUESTION 9:
A cybersecurity administrator needs to add disk redundancy for a critical server. The solution must have a two-drive failure for better fault tolerance. Which of the following RAID levels should the administrator select?
A. 0
B. 1
C. 5
D. 6
QUESTION 10:
A smart retail business has a local store and a newly established and growing online storefront. A recent storm caused a power outage to the business and the local ISP, resulting in several hours of lost sales and delayed order processing.
The business owner now needs to ensure two things:
1.
Protection from power outages
2.
Always-available connectivity In case of an outage
The owner has decided to implement battery backups for the computer equipment Which of the following would BEST fulfill the owner\’s second need?
A. Lease a point-to-point circuit to provide dedicated access.
B. Connect the business router to its own dedicated UPS.
C. Purchase services from a cloud provider for high availability
D. Replace the business\’s wired network with a wireless network.
QUESTION 11:
An organization is concerned about intellectual property theft by employees who leaves the organization. Which of the following will be the organization MOST likely to implement?
A. CBT
B. NDA
C. MOU
D. AUP
QUESTION 12:
Given the following logs:
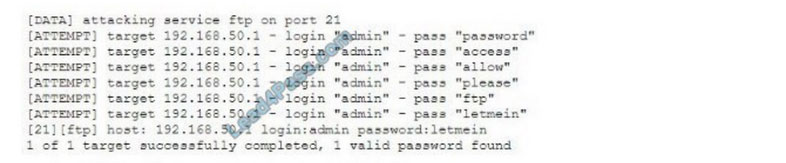
Which of the following BEST describes the type of attack that is occurring?
A. Rainbow table
B. Dictionary
C. Password spraying
D. Pass-the-hash
QUESTION 13:
Ann, a customer, received a notification from her mortgage company stating her PII may be shared with partners, affiliates, and associates to maintain day-to-day business operations.
Which of the following documents did Ann receive?
A. An annual privacy notice
B. A non-disclosure agreement
C. A privileged-user agreement
D. A memorandum of understanding
……
Publish the answer:
| Number: | Answers: | Explain: |
| Q1 | AC | A – “analyst needs to review the first transactions quickly” C – “search the entire series of requests for a particular string” |
| Q2 | D | |
| Q3 | B | Application whitelisting is the practice of specifying an index of approved software applications or executable files that are permitted to be present and active on a computer system. The goal of whitelisting is to protect computers and networks from potentially harmful applications. In general, a whitelist is an index of approved entities. In information security (infosec), whitelisting works best in centrally managed environments, where systems are subject to a consistent workload. https://searchsecurity.techtarget.com/definition/application-whitelisting |
| Q4 | A | |
| Q5 | D | |
| Q6 | C | |
| Q7 | B | |
| Q8 | AF | |
| Q9 | B | |
| Q10 | C | |
| Q11 | B | |
| Q12 | C | |
| Q13 | A |
[Google Drive] Download the sy0-601 dumps question and answers above:https://drive.google.com/file/d/1_ij2vKQ_V5lWRMAfyPhC_vzDXyIPfzHI/
The CompTIA Security+ certification exam has undergone many changes, SY0-101, SY0-201, SY0-301, SY0-401, SY0-501 to now SY0-601, no matter when you use Lead4Pass
Dumps materials are available to help you successfully pass the objective exam. To pass the CompTIA Security+ certification exam today, just download the SY0-601 dumps from https://www.leads4pass.com/sy0-601.html and make sure you pass the exam 100%.