Hi, everyone!
CompTIA PenTest+ PT0-003 was officially released on December 17 last year, which means the past PT0-002 exam will soon be retired!
Don’t be surprised!
All CompTIA certification exams are reissued every three years! And it comes with some updates.
So what is the difference between the latest PT0-003 certification exam and the previous one?
Compare the differences individually:

It can be clearly seen from the table and picture above that PT0-003 has made some very important updates compared to PT0-002, especially the technical operations and attack execution capabilities for specific tasks during the penetration testing process.
In addition to retaining planning and compliance requirements, specific technical operations such as enumeration and reconnaissance, vulnerability analysis, attack execution, and data extraction are added, making the description more practical and emphasizing the ability to attack and obtain data.
There is also a small detail. The PT0-003 exam has added 5 more test questions without changing the test time. This will greatly increase the difficulty of the test and the time to answer the questions.
How should we prepare as candidates?
There are many ways to prepare for the exam on the Internet, buy books, video tutorials, online training and more. But please remember that to pass the PT0-003 exam, you must not use old learning materials. What is truly effective is the latest learning materials.
Now I will share the latest PT0-003 dumps exam questions and answers. In response to the new changes, we have also made new materials to ensure that you can study easily and pass the exam smoothly.
Read the latest list of PT0-003 dumps:
| Total Questions | 234 |
| Single & multiple Choice | 222 |
| Drag Drop | 5 |
| Hotsopt | 2 |
| Simulation Labs | 5 |
| Updated on | Feb 06, 2025 |
The above are the complete PT0-003 dumps exam questions and answers. You can choose PDF or VCE learning tools on Leads4Pass to help you practice the test. VCE provides real-life scenario simulation tests. Both learning methods provide complete learning materials.
Keep reading, below I will share some latest CompTIA PenTest+ PT0-003 dumps exam questions for free.
Latest CompTIA PenTest+ PT0-003 dumps exam questions
Question 1:
A penetration tester has prepared the following phishing email for an upcoming penetration test:

Which of the following is the penetration tester using MOST to influence phishing targets to click on the link?
A. Familiarity and likeness
B. Authority and urgency
C. Scarcity and fear
D. Social proof and greed
Correct Answer: B
Question 2:
A penetration tester initiated the transfer of a large data set to verify a proof-of-concept attack as permitted by the ROE. The tester noticed the client\’s data included PII, which is out of scope, and immediately stopped the transfer.
Which of the following MOST likely explains the penetration tester\’s decision?
A. The tester had the situational awareness to stop the transfer.
B. The tester found evidence of prior compromise within the data set.
C. The tester completed the assigned part of the assessment workflow.
D. The tester reached the end of the assessment time frame.
Correct Answer: A
Situational awareness is the ability to perceive and understand the environment and events around oneself, and to act accordingly. The penetration tester demonstrated situational awareness by stopping the transfer of PII, which was out of scope and could have violated the ROE or legal and ethical principles. The other options are not relevant to the situation or the decision of the penetration tester.
Question 3:
A Chief Information Security Officer wants to evaluate the security of the company\’s e- commerce application.
Which of the following tools should a penetration tester use FIRST to obtain relevant information from the application without triggering alarms?
A. SQLmap
B. DirBuster
C. w3af
D. OWASP ZAP
Correct Answer: C
W3AF, the Web Application Attack and Audit Framework, is an open source web application security scanner that includes directory and filename bruteforcing in its list of capabilities.
Question 4:
In a cloud environment, a security team discovers that an attacker accessed confidential information that was used to configure virtual machines during their initialization. Through which of the following features could this information have been accessed?
A. IAM
B. Block storage
C. Virtual private cloud
D. Metadata services
Correct Answer: D
In a cloud environment, the information used to configure virtual machines during their initialization could have been accessed through metadata services.
Metadata Services:
Other Features:
Pentest References:
Cloud Security: Understanding how metadata services work and the potential risks associated with them is crucial for securing cloud environments. Exploitation: Metadata services can be exploited to retrieve sensitive data if not properly secured.
By accessing metadata services, an attacker can retrieve sensitive configuration information used during VM initialization, which can lead to further exploitation.
Question 5:
During a penetration testing engagement, a tester targets the internet-facing services used by the client. Which of the following describes the type of assessment that should be considered in this scope of work?
A. Segmentation
B. Mobile
C. External
D. Web
Correct Answer: C
An external assessment focuses on testing the security of internet-facing services. Here\’s why option C is correct:
External Assessment: It involves evaluating the security posture of services exposed to the internet, such as web servers, mail servers, and other public-facing infrastructure.
The goal is to identify vulnerabilities that could be exploited by attackers from outside the organization\’s network.
Segmentation: This type of assessment focuses on ensuring that different parts of a network are appropriately segmented to limit the spread of attacks. It\’s more relevant to internal network architecture.
Mobile: This assessment targets mobile applications and devices, not general internet-facing services.
Web: While web assessments focus on web applications, the scope of an external assessment is broader and includes all types of internet-facing services.
References from Pentest:
Horizontall HTB: Highlights the importance of assessing external services to identify vulnerabilities that could be exploited from outside the network. Luke HTB: Demonstrates the process of evaluating public-facing services to ensure their security.
Conclusion:
Option C, External, is the most appropriate type of assessment for targeting internet-facing services used by the client.
Question 6:
A security engineer is trying to bypass a network IPS that isolates the source when the scan exceeds 100 packets per minute. The scope of the scan is to identify web servers in the 10.0.0.0/16 subnet.
Which of the following commands should the engineer use to achieve the objective in the least amount of time?
A. nmap -T3 -p 80 10.0.0.0/16 — max-hostgroup 100
B. nmap -TO -p 80 10.0.0.0/16
C. nmap -T4 -p 80 10.0.0.0/16 — max-rate 60
D. nmap -T5 -p 80 10.0.0.0/16 — min-rate 80
Correct Answer: C
The nmap -T4 -p 80 10.0.0.0/16 — max-rate 60 command is used to scan the 10.0.0.0/16 subnet for web servers (port 80) at a maximum rate of 60 packets per minute. The -T4 option sets the timing template to “aggressive”, which speeds up the scan.
The — max-rate option limits the number of packets sent per second, helping to bypass the network IPS that isolates the source when the scan exceeds 100 packets per minute12.
Question 7:
During passive reconnaissance of a target organization\’s infrastructure, a penetration tester wants to identify key contacts and job responsibilities within the company.
Which of the following techniques would be the most effective for this situation?
A. Social media scraping
B. Website archive and caching
C. DNS lookup
D. File metadata analysis
Correct Answer: A
Social media scraping involves collecting information from social media platforms where employees might share their roles, responsibilities, and professional affiliations. This method can reveal detailed insights into the organizational structure, key personnel, and specific job functions within the target organization, making it an invaluable tool for understanding the company\’s internal landscape without alerting the target to the reconnaissance activities.
Question 8:
A penetration tester is performing an assessment against a customer\’s web application that is hosted in a major cloud provider\’s environment. The penetration tester observes that the majority of the attacks attempted are being blocked by the organization\’s WAF.
Which of the following attacks would be most likely to succeed?
A. Reflected XSS
B. Brute-force
C. DDoS
D. Direct-to-origin
Correct Answer: D
Question 9:
Which of the following tools would be best to use to conceal data in various kinds of image files?
A. Kismet
B. Snow
C. Responder
D. Metasploit
Correct Answer: B
Snow is a tool designed for steganography, which is the practice of concealing messages or information within other non-secret text or data. In this context, Snow is specifically used to hide data within whitespace of text files, which can include the whitespace areas of images saved in formats that support text descriptions or metadata, such as certain PNG or JPEG files.
While the other tools listed (Kismet, Responder, Metasploit) are powerful in their respective areas (network sniffing, LLMNR/NBT-NS poisoning, and exploitation framework), they do not offer functionality related to data concealment in image files or steganography.
Question 10:
A penetration tester ran a simple Python-based scanner. The following is a snippet of the code: Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization\’s IDS?
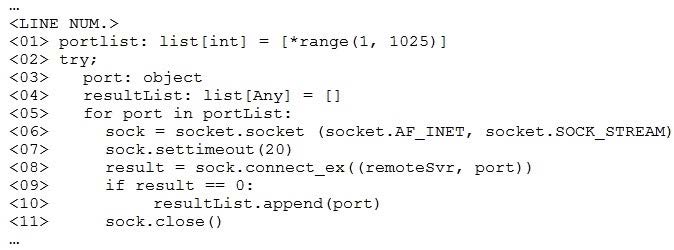
A. sock.settimeout(20) on line 7 caused each next socket to be created every 20 milliseconds.
B. *range(1, 1025) on line 1 populated the portList list in numerical order.
C. Line 6 uses socket.SOCK_STREAM instead of socket.SOCK_DGRAM
D. The remoteSvr variable has neither been type-hinted nor initialized.
Correct Answer: B
Port randomization is widely used in port scanners. By default, Nmap randomizes the scanned port order (except that certain commonly accessible ports are moved near the beginning for efficiency reasons) https://nmap.org/book/man-portspecification.html
Question 11:
A penetration tester needs to help create a threat model of a custom application. Which of the following is the most likely framework the tester will use?
A. MITRE ATTandCK
B. OSSTMM
C. CI/CD
D. DREAD
Correct Answer: D
The DREAD model is a risk assessment framework used to evaluate and prioritize the security risks of an application. It stands for Damage potential, Reproducibility, Exploitability, Affected users, and Discoverability.
Understanding DREAD:
Usage in Threat Modeling:
Process:
References from Pentesting Literature:
Step-by-Step ExplanationReferences:
Penetration Testing – A Hands-on Introduction to Hacking HTB Official Writeups
Question 12:
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
A. Articulation of cause
B. Articulation of impact
C. Articulation of escalation
D. Articulation of alignment
Correct Answer: B
When concluding a penetration test, effectively communicating the need for vulnerability remediation is crucial. Here\’s why the articulation of impact is the most important aspect:
Articulation of Cause (Option A):
Articulation of Impact (Option B):
Articulation of Escalation (Option C):
Articulation of Alignment (Option D):
Conclusion: Articulating the impact of vulnerabilities is the most crucial element when communicating the need for remediation.
By clearly explaining the potential risks and consequences, penetration testers can effectively convey the urgency and importance of addressing the discovered issues, thus motivating clients to take prompt and appropriate action.
Question 13:
During an assessment, a penetration tester obtains a list of 30 email addresses by crawling the target company\’s website and then creates a list of possible usernames based on the email address format. Which of the following types of attacks would MOST likely be used to avoid account lockout?
A. Mask
B. Rainbow
C. Dictionary
D. Password spraying
Correct Answer: D
Password spraying is a type of password guessing attack that involves trying one or a few common passwords against many usernames or accounts.
Password spraying can avoid account lockout policies that limit the number of failed login attempts per account by spreading out the attempts over time and across different accounts.
Password spraying can also increase the chances of success by using passwords that are likely to be used by many users, such as default passwords, seasonal passwords, or company names.
Mask is a type of password cracking attack that involves using a mask or a pattern to generate passwords based on known or guessed characteristics of the password, such as length, case, or symbols. Rainbow is a technique of storing precomputed hashes of passwords in a table that can be used to quickly crack passwords by looking up the hashes.
Dictionary is a type of password cracking attack that involves using a wordlist or a dictionary of common or likely passwords to try against an account.
Question 14:
A penetration tester is conducting reconnaissance for an upcoming assessment of a large corporate client. The client authorized spear phishing in the rules of engagement.
Which of the following should the tester do first when developing the phishing campaign?
A. Shoulder surfing
B. Recon-ng
C. Social media
D. Password dumps
Correct Answer: C
When developing a phishing campaign, the tester should first use social media to gather information about the targets.
Social Media:
Process:
Other Options:
Pentest References:
Spear Phishing: A targeted phishing attack aimed at specific individuals, using personal information to increase the credibility of the email.
OSINT (Open Source Intelligence): Leveraging publicly available information to gather intelligence on targets, including through social media. By starting with social media, the penetration tester can collect detailed and personalized information about the targets, which is essential for creating an effective spear phishing campaign.
Question 15:
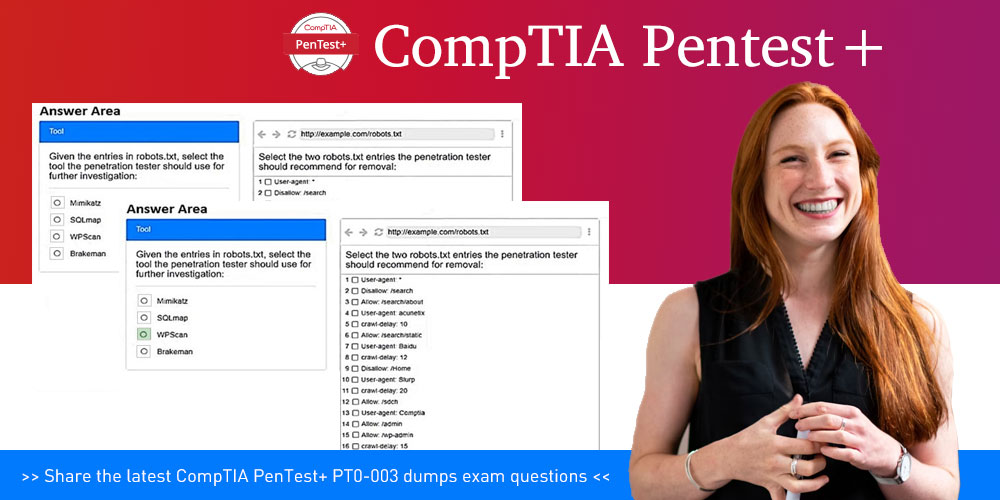
HOTSPOT
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:

Correct Answer:

Explanation:
The tool the penetration tester should use for the further investigation is WPScan The two entries in the robots.txt file that the penetration tester should recommend for removal are 14 Allow: /admin 15 Allow: /wp-admin
PT0-003 dumps PDF online download
Download the latest CompTIA PenTest+ PT0-003 dumps exam questions above and practice the test anytime, anywhere: https://drive.google.com/file/d/1GxU9E4uDxTSrpaN_dw2PB6Q0MB0QYZwm/view?usp=sharing
Summarize
Passing the newly released CompTIA Pentest+ PT0-003 exam isn’t easy! Compared with the previous PT0-002 exam, it will be more difficult!
In particular, the core technologies of technical operations and attack execution capabilities in the penetration testing process have been greatly upgraded, so candidates are recommended to use the Latest CompTIA PenTest+ PT0-003 dumps exam questions: https://www.leads4pass.com/pt0-003.html to help them succeed in the exam.