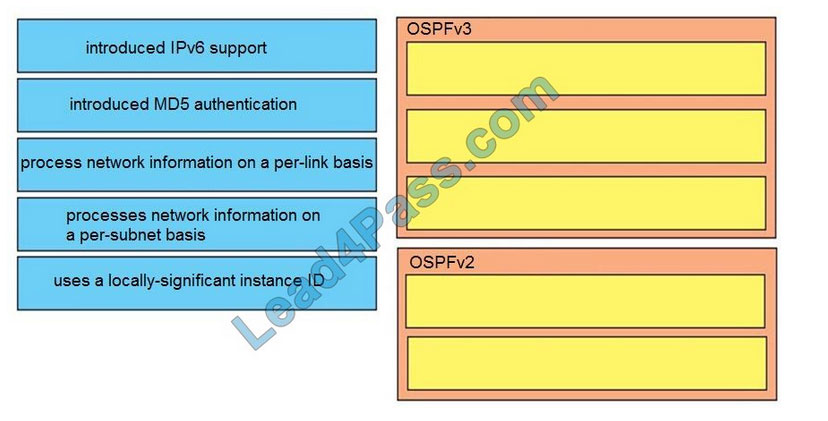
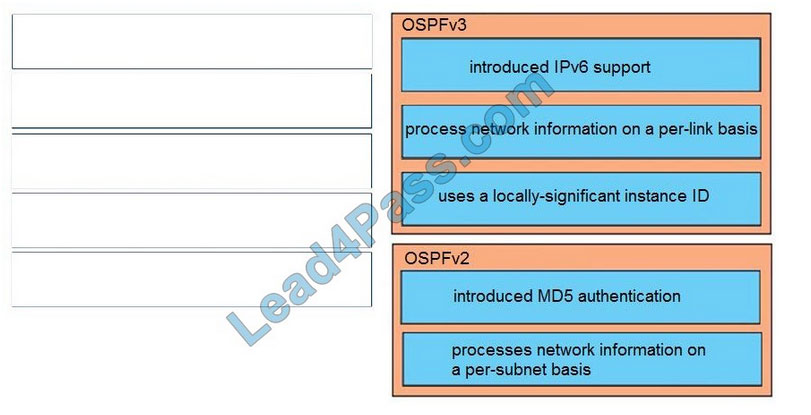
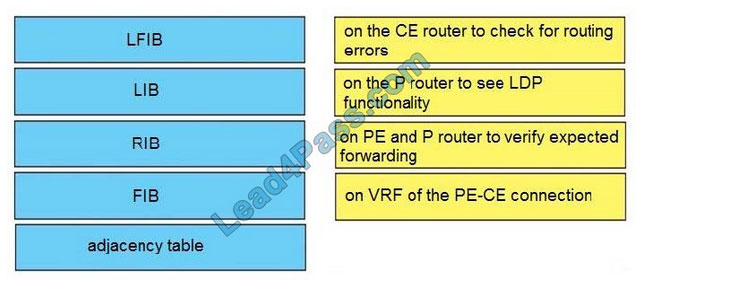
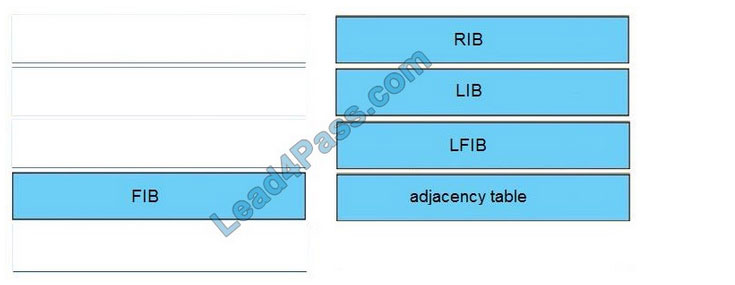
The newly updated Citrix 1Y0-341 dumps contains 107 exam questions and answers that candidates can study using the 1Y0-341 dumps PDF and 1Y0-341 dumps VCE to help you successfully pass the 1Y0-341 CCP-N exam.
You are welcome to download the latest Citrix 1Y0-341 dumps: https://www.leads4pass.com/1y0-341.html, Lead4Pass 1Y0-341 dumps serve all candidates taking the 1Y0-341 CCP-N exam and guarantee you 100% Successfully passed the 1Y0-341 CCP-N exam.
Download the Citrix 1Y0-341 PDF for free sharing online:
https://drive.google.com/file/d/1s5eav8OByBa2WbY1S19OtiuDYNsVNAHt/
Share the latest Citrix 1Y0-341 dumps exam questions and answers for free
New Question 1:
A Citrix Engineer needs to set up access to an internal application for external partners.
Which two entities must the engineer configure on the Citrix ADC to support this? (Choose two.)
A. SAML Policy
B. SAMLldP Profile
C. SAMLldP Policy
D. SAML Action
Correct Answer: AB
New Question 2:
Which action ensures that content is retrieved from the server of origin?
A. CACHE
B. MAY_CACHE
C. NOCACHE
D. MAY_NOCACHE
Correct Answer: C
New Question 3:
Scenario: A Citrix Engineer configures Citrix Web App Firewall to protect an application. Users report that they are NOT able to log on. The engineer enables a Start URL relaxation for the path //login.aspx.
What is the effect of the Start URL relaxation on the application?
A. Access to the path /login.aspx is unblocked.
B. Access to the path /login.aspx is blocked.
C. External users are blocked from the path /login.aspx. Internal users are permitted to the path / login.aspx.
D. Non-administrative users are blocked from the path /login.aspx Administrative users are permitted to the path /login.aspx.
Correct Answer: A
New Question 4:
Scenario: A Citrix Engineer wants to protect a web application using Citrix Web App Firewall. The engineer enables the Learn action for the Start URL, HTML, Cross-Site Scripting, and HTML SQL Injection protections. The engineer assigns this profile to a policy, which is then bound to the virtual server.
Which two items can the engineer check to determine that the Learn action is NOT capturing any rules? (Choose two.)
A. The HTML Error Object is configured for the profile.
B. Enough space is left on the /flash file system.
C. The aslearn process is running on the Citrix ADC appliance.
D. The Learn database is less than 20 MB.
Correct Answer: AC
New Question 5:
A Citrix Engineer wants to delegate management of Citrix Application Delivery Management (ADM) to a junior team member.
Which assigned role will limit the team member to view all application-related data?
A. readonly
B. appReadonly
C. admin
D. appAdmin
Correct Answer: B
New Question 6:
A Citrix Engineer wants the Citrix Web App Firewall to respond with a page stored on the Citrix ADC when a violation is detected.
Which profile setting accomplishes this?
A. Redirect URL
B. RFC Profile
C. Default Request
D. HTML Error Object
Correct Answer: D
Reference: https://support.citrix.com/article/CTX140293
New Question 7:
Scenario: A Citrix Engineer has a pair of Citrix ADC VPX appliances configured as a High- Availability (HA) pair and hosted on a Citrix Hypervisor. The engineer wants to use Citrix Application Delivery Management (ADM) to monitor and manage the 35 web applications on the appliances. The engineer has imported Citrix ADM virtual appliance to Citrix Hypervisor. The engineer has also configured the management IP address settings and has added 35 instances. However, some of the instances are NOT reporting any data.
Which two areas can the engineer check to determine the cause of the issue? (Choose two.)
A. A Premium platform license must be configured on each instance.
B. AppFlow must be enabled on each instance.
C. The Citrix ADM license must be installed.
D. An SSL certificate must be installed on the Citrix ADM appliance.
Correct Answer: CD
New Question 8:
Scenario: A Citrix Engineer implements Application-level Quality of Experience (AppQoE) to protect a web application. Shortly after that, users call to complain that nearly every request is being met with a Captcha.
What can the engineer do to improve the user experience?
A. Disable the Captcha.
B. Increase the DOS Attack Threshold.
C. Increase the Policy Queue Depth.
D. Increase the Session Life.
Correct Answer: B
New Question 9:
In which order is a client request to a protected web application processed?
A. CitrixWebApp Firewall, Load Balancing, Caching, Rewrite
B. Caching, Citrix Web App Firewall, Load Balancing, Rewrite
C. Citrix Web App Firewall, Caching, Load Balancing, Rewrite
D. Load Balancing, Citrix Web App Firewall, Caching, Rewrite
Correct Answer: C
New Question 10:
Which Citrix Application Delivery Management (ADM) Analytics page allows an engineer to monitor the metrics of end-point analysis and authentication failures?
A. Gateway Insight
B. HDX Insight
C. Web Insight
D. Security Insight
Correct Answer: A
New Question 11:
Scenario: A Citrix Engineer creates a Responder policy to redirect users attempting to access an application protected by Citrix Web App Firewall. Instead of being redirected, users are seeing an `Access Denied\’ page.
This is happening because Citrix Web App Firewall is processed. (Choose the correct option to complete the sentence.)
A. before Responder, and the redirection is invalid
B. after Responder, but the violation is applied to prevent access
C. before Responder, and a violation is occurring
D. after Responder, and the redirection is invalid
Correct Answer: C
New Question 12:
Scenario: A Citrix Engineer is reviewing the Citrix Web App Firewall log files using the GUI. Upon further analysis, the engineer notices that legitimate application traffic is being blocked.
What can the engineer do to allow the traffic to pass through while maintaining security?
A. Note the protection blocking the traffic in the log entry. Edit the profile and deselect the Block action for protection.
B. Select the check box in the log entry. Choose to Dismiss to allow the traffic to pass through from the Action menu.
C. Note the protection blocking the traffic in the log entry. Create a new profile and policy and bind it with a larger priority number.
D. Select the check box in the log entry. Choose Edit and Deploy to create a relaxation rule from the Action menu.
Correct Answer: D
New Question 13:
Scenario: A Citrix Engineer is monitoring the environment with Citrix Application Delivery Management (ADM). Management has asked for a report of high-risk traffic to protected internal websites.
Which dashboard can the engineer use to generate the requested report?
A. App Security
B. Transactions
C. Users and Endpoints
D. App
Correct Answer: B
New Question 14:
Scenario: A Citrix Engineer has configured Citrix Application Delivery Management (ADM) to monitor applications presented by Citrix ADC appliances. When reviewing the App Security Dashboard, the engineer finds no data.
What must the engineer do to ensure data is being collected from the applications?
A. Enable AppFlow for Security Insight on the instances in Citrix ADM.
B. Update the password stored in the instance profile on Citrix ADM.
C. Point the default route on Citrix ADM to the subnet with the NSIPs of the Citrix ADC appliances.
D. Enable the Web App Firewall feature on the Citrix ADC appliances.
Correct Answer: A
New Question 15:
Scenario: A Citrix Engineer configured signature protections for Citrix Web App Firewall. Signature Auto-Update has been enabled. Upon reviewing the log files, the engineer notices that the auto-update process has an error. In the settings for Signature Auto Update, the engineer notices that the URL is blank.
Which URL should the engineer enter to restore the update process?
A. https://s3.amazonaws.com/NSAppFwSignatures/SignaturesMapping.xml
B. https://download.citrix.com/NSAppFwSignatures/SignaturesMapping.xml
C. https://www.citrix.com/NSAppFwSignatures/SignaturesMapping.xml
D. https://citrix.azure.com/NSAppFwSignatures/SignaturesMapping.xml
Correct Answer: A
Reference: https://support.citrix.com/article/CTX138858
…
Download the Citrix 1Y0-341 PDF for free sharing online:
https://drive.google.com/file/d/1s5eav8OByBa2WbY1S19OtiuDYNsVNAHt/
The above is only a part of Citrix 1Y0-341 dumps exam questions and answers, you can use the above exam questions and answers to improve yourself, not only that, we welcome you to download the latest
Citrix 1Y0-341 dumps exam questions: https://www.leads4pass.com/1y0-341.html (Total Questions: 107 Q&A), help you truly pass the 1Y0-341 CCP-N exam.
More IT certification blogs: [Amazon]awsexamdumps.com, [Oracle]oraclefreedumps.com, [Citrix]Citrixfreedumps.com, [Microsoft]examdumpsbase.com, [Citrix]citrixexamdumps.com
[Citrix]Citrixfreedumps.com, [VMware]vmwarefreedumps.com, [IBM]ibmexamdumps.com, [HP]hpexamdumps.com, [NetApp]netappexamdumps.com, [Juniper]juniperexamdumps.com
[Fortinet]fortinetexamdumps.com