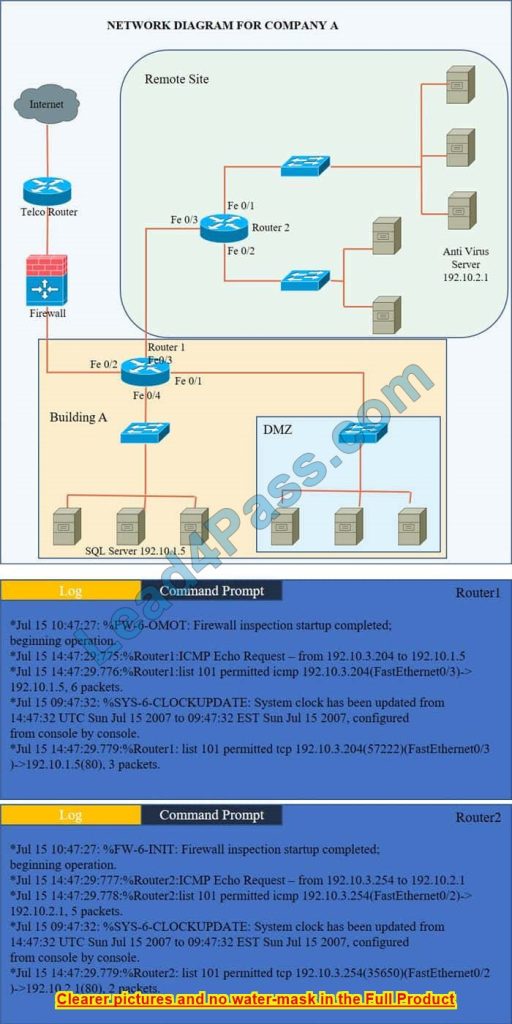
CCNA 200-301 dumps are the latest and most effective exam solution to aid candidates in their pre-exam practice!
CCNA 200-301 dumps have been updated! Reviewed, corrected, and actually verified by the Cisco team, it is true and effective! Meet the conditions for successfully passing the CCNA certification exam.
CCNA 200-301 dumps contain 1205 latest exam questions and answers, which truly cover all CCNA core exam requirements (Network fundamentals, Network access, IP connectivity, IP services, Security fundamentals, Automation, and programmability).
Use the latest and effective CCNA certification exam solution, and download CCNA 200-301 dumps with PDF and VCE: https://www.leads4pass.com/200-301.html to help you study easily and successfully pass the CCNA certification exam.
And share some CCNA 200-301 dumps exam questions online practice for free:
| From | Number of exam questions | Online Download | Associated certification |
| Lead4Pass | 15 | 200-301 PDF | CCNA, CCNP |
Question 1:
After you deploy a new WLAN controller on your network, which two additional tasks should you consider? (Choose two.)
A. deploy load balancers
B. configure additional vlans
C. configure multiple VRRP groups
D. deploy POE switches
E. configure additional security policies
Correct Answer: AE
Question 2:
A router received three destination prefixes: 10.0.0.0/8, 10.0.0.0/16, and 10.0.0.0/24. When the show ip route command is executed, which output does it return?
A. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/8 [110/5] via 192.168.1.1, 0:01:00, Ethernet0
o E2 10.0.0.0/16[110/5] via 192.168.2.1, 0:01:00, Ethernet1
o E2 10.0.0.0/24[110/5] via 192.168.3.1, 0:01:00, Ethernet2
B. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/8 [110/5] via 192.168.1.1, 0:01:00, Ethernet0
C. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/24[110/5] via 192.168.3.1, 0:01:00, Ethernet2
D. Gateway of last resort is 172.16.1.1 to network 0.0.0.0
o E2 10.0.0.0/16[110/5] via 192.168.2.1, 0:01:00, Ethernet1
o E2 10.0.0.0/24[110/5] via 192.168.3.1, 0:01:00, Ethernet2
Correct Answer: A
Question 3:
Which three describe the reasons large OSPF networks use a hierarchical design? (Choose three.)
A. to speed up convergence
B. to reduce routing overhead
C. to lower costs by replacing routers with distribution layer switches
D. to decrease latency by increasing bandwidth
E. to confine network instability to single areas of the network
F. to reduce the complexity of router configuration
Correct Answer: ABE
Question 4:
Which two protocols must be disabled to increase security for management connections to a Wireless LAN Controller? (Choose two)
A. Telnet
B. SSH
C. HTTP
D. HTTPS
E. TFTP
Correct Answer: AC
Question 5:
Which cable type must be used to interconnect one switch using 1000 BASE-SX GBIC modules and another switch using 1000 BASE-SX SFP modules?
A. LC to SC
B. SC to SC
C. LC to LC
D. SC to ST
Correct Answer: D
Question 6:
Which two actions influence the EIGRP route selection process? (Choose two.)
A. The advertised distance is calculated by a downstream neighbor to inform the local router of the bandwidth on the link.
B. The router calculates the feasible distance of all paths to the destination route.
C. The router must use the advertised distance as the metric for any given route.
D. The router calculates the best backup path to the destination route and assigns it as the feasible successor.
E. The router calculates the reported distance by multiplying the delay on the exiting interface by 256.
Correct Answer: BD
The reported distance (or advertised distance) is the cost from the neighbor to the destination.
It is calculated from the router advertising the route to the network. For example in the topology below, suppose routers A and B are exchanging their routing tables for the first time.
Router B says “Hey, the best metric (cost) from me to IOWA is 50 and the metric from you to IOWA is 90” and advertises it to router A.
Router A considers the first metric (50) as the Advertised distance. The second metric (90), which is from NEVADA to IOWA (through IDAHO), is called the Feasible distance.
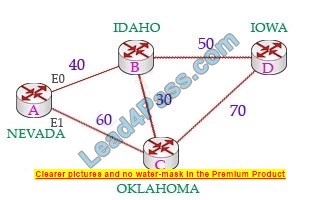
The reported distance is calculated in the same way as calculating the metric. By default (K1 = 1, K2 = 0, K3 = 1, K4 = 0, K5 = 0), the metric is calculated as follows:

A feasible successor is a backup route. To be a feasible successor, the route must have an Advertised distance (AD) less than the Feasible distance (FD) of the current successor route.
Feasible distance (FD): The sum of the AD plus the cost between the local router and the next-hop router. The router must calculate the FD of all paths to choose the best path to put into the routing table.
Note: Although the new CCNA exam does not have an EIGRP topic you should learn the basic knowledge of this routing protocol.
Question 7:
Which two transport layer protocols carry syslog messages? (Choose two.)
A. IP
B. RTP
C. TCP
D. UDP
E. ARP
Correct Answer: CD
Question 8:
Which action implements physical access control as part of the security program of an organization?
A. setting up IP cameras to monitor key infrastructure
B. configuring a password for the console port
C. backing up Syslogs at a remote location
D. configuring enable passwords on network devices
Correct Answer: A
Question 9:
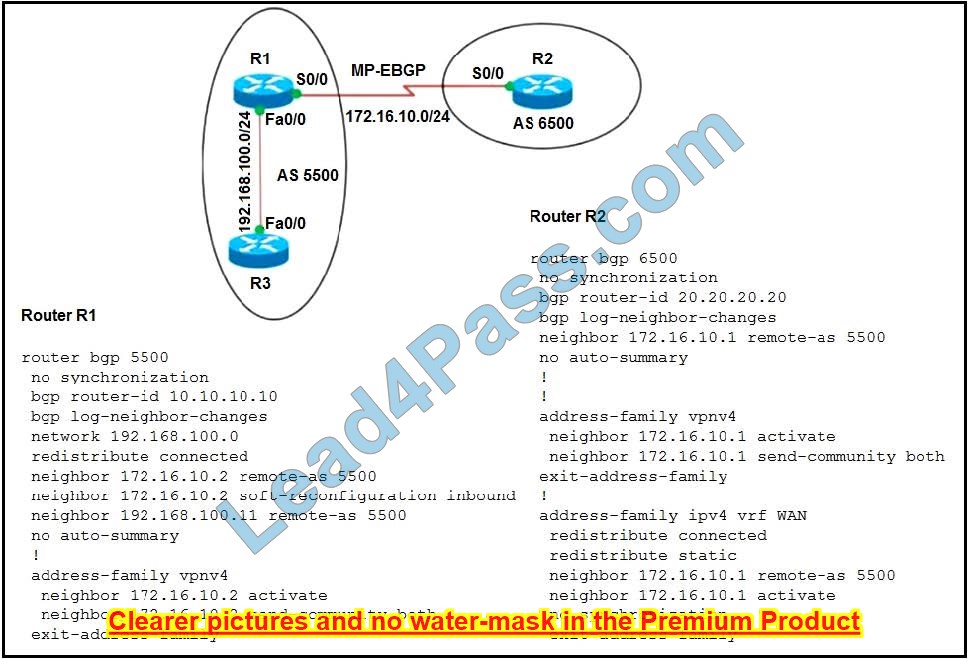
Refer to Exhibit. Which configuration must be applied to the router that configures PAT to translate all addresses in VLAN 200 while allowing devices on VLAN 100 to use their own IP addresses?
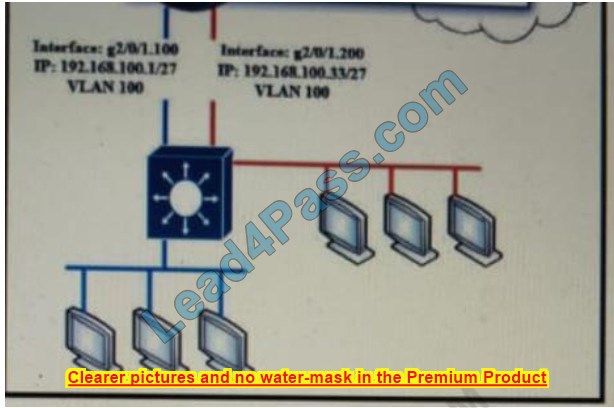
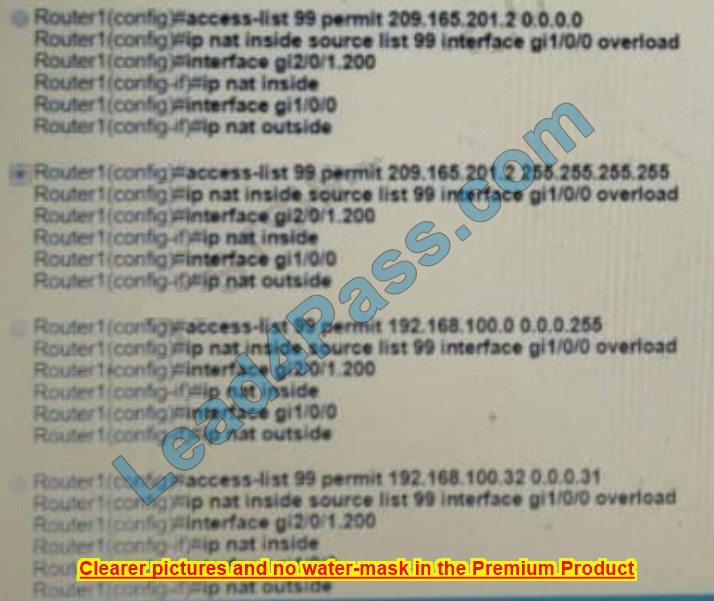
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
Question 10:
What does an SDN controller use as a communication protocol to relay forwarding changes to a southbound API?
A. OpenFlow
B. Java
C. REST
D. XML
Correct Answer: A
Question 11:
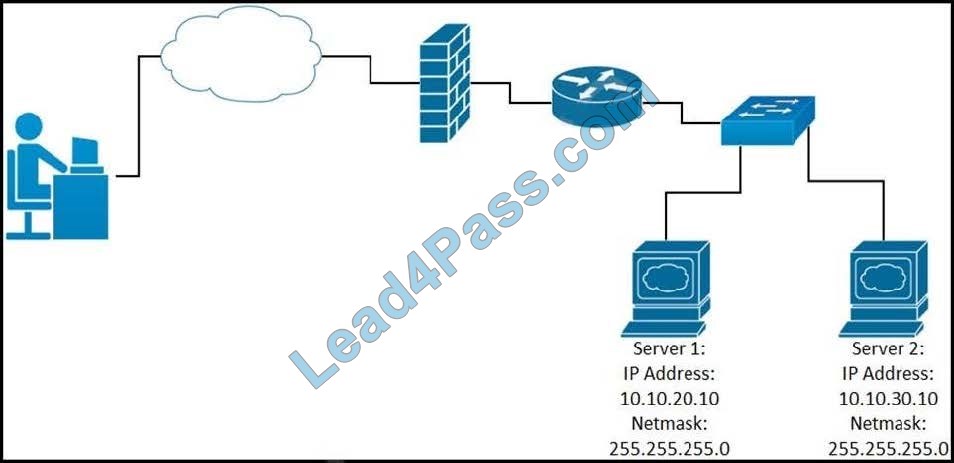
Refer to the exhibit. Traffic sourced from the loopback0 Interface is trying to connect via ssh to the host at 10.0.1.15. What Is the next hop to the destination address?
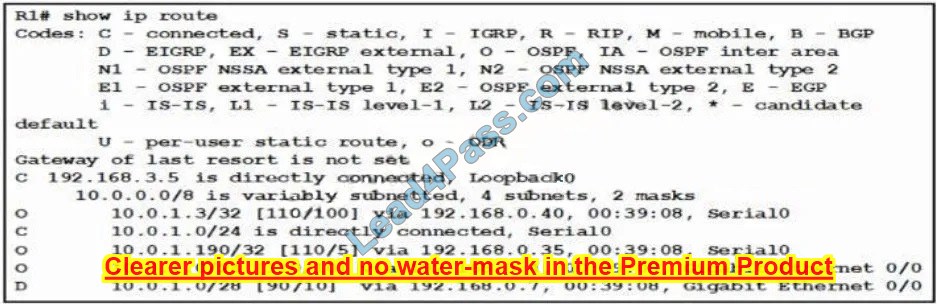
A. 192.168.0.7
B. 192.168.0.4
C. 192.168.0.40
D. 192.168.3.5
Correct Answer: B
Question 12:
What does WPA3 provide in wireless networking?
A. backward compatibility with WPA and WPA2
B. safeguards against brute force attacks with SAE
C. increased security and requirement of a complex configuration
D. optional Protected Management Frame negotiation
Correct Answer: B
Question 13:
When router R1 receives a packet with destination IP address 10.56.0 62. through which interface does it route the packet?
A. Null0
B. VIan58
C. Vlan60
D. VIan59
Correct Answer: B
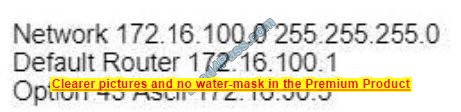
Question 14:
Refer to the exhibit.
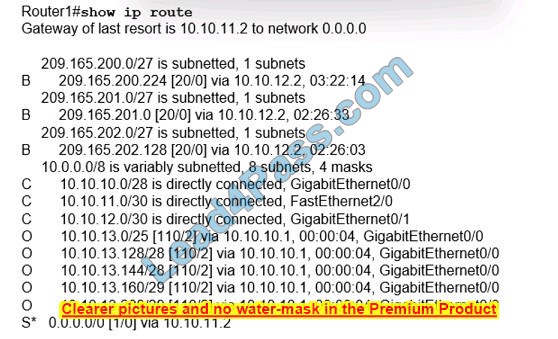
What is the subnet mask of the route to the 10.10.13.160 prefix?
A. 255.255.255.240
B. 255.255.255.128
C. 255.255.248.
D. 255.255.255.248
Correct Answer: D
Question 15:
Which protocol does an access point used to draw power from a connected switch?
A. Internet Group Management Protocol
B. Adaptive Wireless Path Protocol
C. Cisco Discovery Protocol D. Neighbor Discovery Protocol
Correct Answer: C
…
CCNA 200-301 dumps help you take an important step toward a networking career! Using the latest and most effective CCNA certification exam program can not only make you progress quickly but also ensure that you can pass the exam 100% successfully.
You can take advantage of free CCNA 200-301 exam dumps to help you verify your current learning and improve your professional knowledge! Download 100% Best CCNA Certification Exam solution, CCNA 200-301 dumps with PDF and VCE: https://www.leads4pass.com/200-301.html
Really helps you pass the exam 100% successfully!