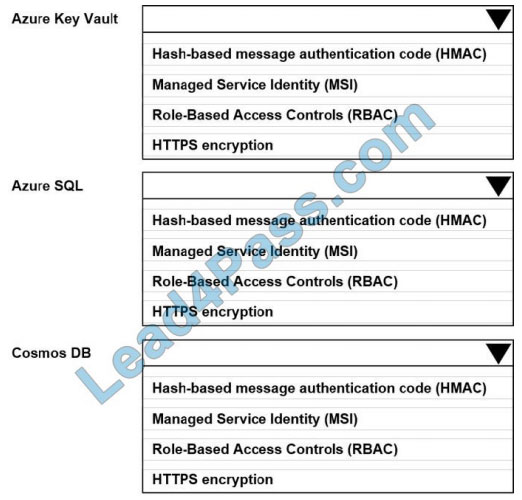
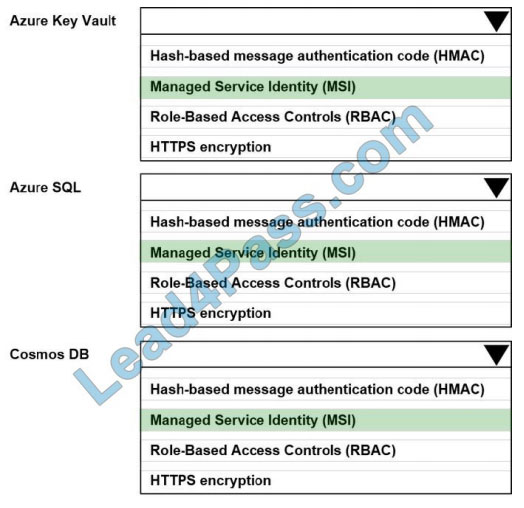
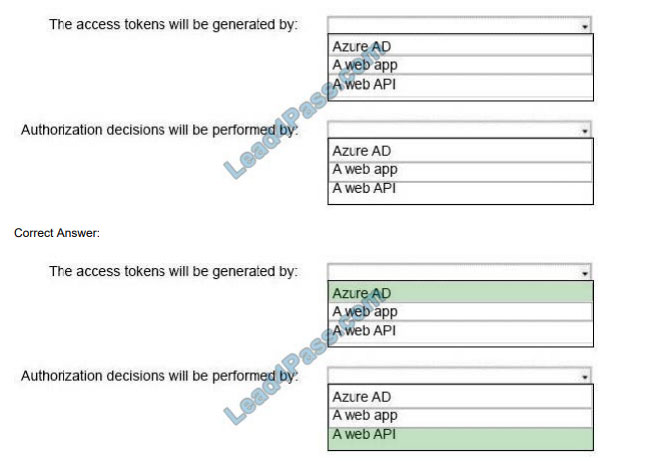
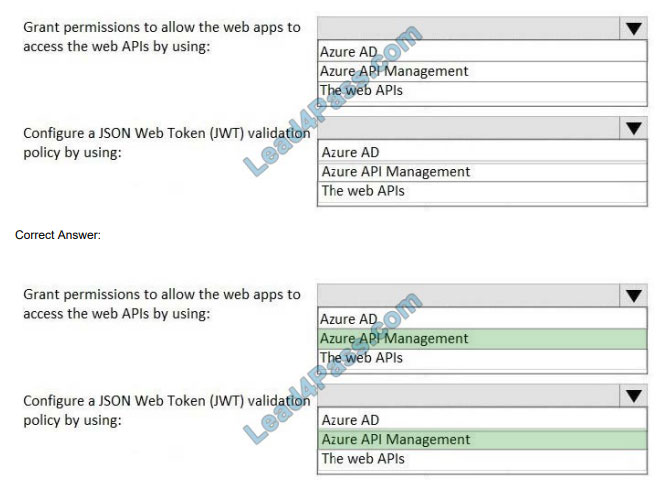
What is the best way to pass the RedHat EX300 exam? (First: Exam practice test, Second: Lead4pass RedHat expert.) You can get free RedHat RHCE certification EX300 exam practice test questions here.
Or choose: https://www.leads4pass.com/rhce-certification.html Study hard to pass the exam easily!
Table of Contents:
Latest RedHat RHCE certification EX300 google drive
[PDF] Free RedHat RHCE certification EX300 pdf dumps download from Google Drive: https://drive.google.com/open?id=1eR3fJCpFXYoqH9dbkH5yg_C9Ewk3_BUI
Red Hat Certified Engineer (RHCE) exam for Red Hat Enterprise Linux 7:https://www.redhat.com/en/services/training/ex300-red-hat-certified-engineer-rhce-exam-red-hat-enterprise-linux-7
The performance-based Red Hat Certified Engineer (RHCE) exam for Red Hat Enterprise Linux 7 (EX300) tests to determine if your knowledge, skill, and ability meet those required of a senior system administrator responsible for Red Hat® Enterprise Linux® systems. Red Hat Certified System Administrator (RHCSA®) certification is required to earn RHCE® certification.
This exam and the exam objectives provided here are based on the Red
Hat Enterprise Linux 7 version of the exam.
An RHCE certification is earned by a Red Hat Certified System Administrator (RHCSA) who has demonstrated the knowledge, skill, and ability required of a senior system administrator responsible for Red Hat Enterprise Linux systems.
Latest updates RedHat EX300 exam practice questions
QUESTION 1
SIMULATION
Configure the nfs server, share the /common directory to domain30.example.com, and allow client to have the root user
right when access as a root user.
A. explanation
Correct Answer: A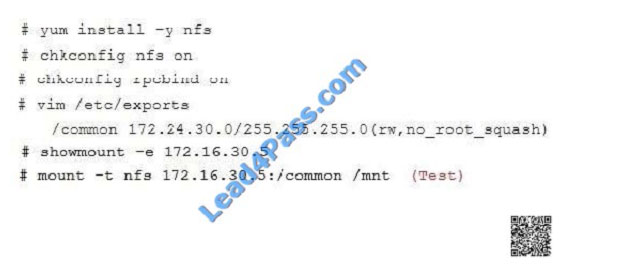
QUESTION 2
SIMULATION
There were two systems: system1, main system on which most of the configuration take place system2, some
configuration here Webpage content modification. Implement website for http://serverX.example.com/owndir Create a
directory named as “owndir” under the document root of webserver Download
http://station.network0.example.com/pub/rhce/restrict.html Rename the file into ondex.html The content of the owndir
should be visible to everyone browsing from your local system but should not be accessible from other location
A. explanation
Correct Answer: A
QUESTION 3
SIMULATION
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Configure selinux.
Configure your systems that should be running in Enforcing.
A. explanation
Correct Answer: A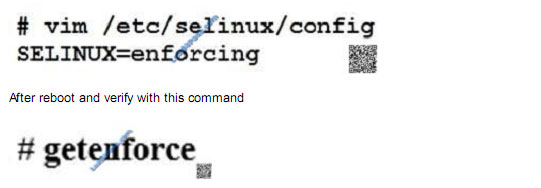
QUESTION 4
SIMULATION
There were two systems: system1, main system on which most of the configuration take place system2, some
configuration here SMTP Configuration. Configure the SMTP mail service on serverX and desktopX which relay the mail
only from local system through station.network0.example.com, all outgoing mail have their sender domain as
example.com. Ensure that mail should not store locally. Verify the mail server is working by sending mail to a natasha
user. Check the mail on both serverX and desktopX with the below URL http://station.network0.example.com/system1
http://station.network0.example.com/system2
A. explanation
Correct Answer: A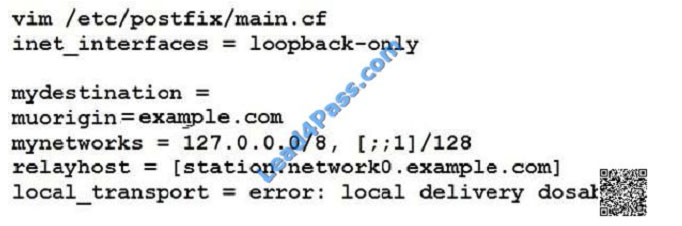
QUESTION 5
SIMULATION
You are working as an Administrator. There is a common data shared (/data) from 192.168.0.254 to all users in your
local LAN. When user\\’s system start, shared data should automatically mount on /common directory.
A. explanation
Correct Answer: A
To automatically mount at boot time, we use the /etc/fstab file. Because /etc/rc.d/rc.sysinit file reads and mounts all file
system specified in /etc/fstab. To mount Network Sharing Files also use the /etc/fstab but filesystem is nfs.
QUESTION 6
SIMULATION
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Script1.
Create a script on serverX called /root/random with the following details
When run as /root/random postconf, should bring the output as “postroll”
When run as /root/random postroll, should bring the output as “postconf”
When run with any other argument or without argument, should bring any other argument or without argument, should
bring the stderr as “/root/random postconf|postroll”
A. explanation
Correct Answer: A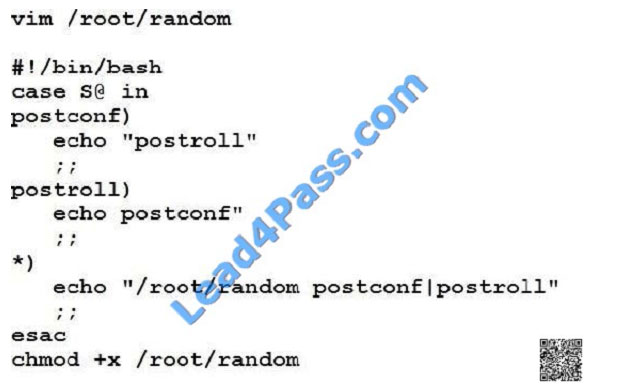
QUESTION 7
SIMULATION
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client.
Password for both of the two systems is atenorth
System\\’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the
following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10 The subnet mask is 255.255.255.0 Your system is a member of DNS
domain group3.example.com. All systems in DNS domain group3.example.com are all in subnet
172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless
specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this
domain, this domain provides the following user account:
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in
separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you
made still can be operated after the restart without manual intervention, virtual machine instances of all examinations
must be able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test
using virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be
found in the following link: http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the
host and network, although you correctly configured the network service but would have to allow the host or network is
blocked, this also does not score.
You will notice that some requirements which clearly do not allow services be accessed by service domain my133t.org,
systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems of these subnets also belong to my
133t.org domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform
a series of restrictions on a user, but this user creation may be required in other questions. For convenient identification,
each exam question has some radio buttons to help you identify which questions you have already completed or not
completed. Certainly, you do not need to care these buttons if you don\\’t need them.
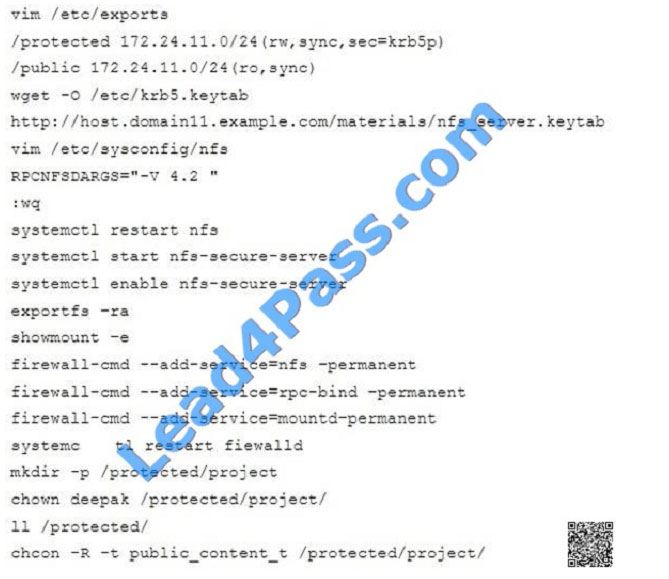
Configure NFS service
Configure the NFS service on the system1, as required:
1.
Share the directory /public in read only way, just can be accessed by systems in domain11.example.com at the same
time.
2.
Share the directory /protected in rad and write way, Kerberos security encryption required, you can use the key
provided by the following URL: http://host.domain11.example.com/materials/nfs_server.keytab
3.
The directory /protected should contain the sub directory named project and the owner name is deepak;
4.
User deepak can access /protected/project in read and write ways
A. explanation
Correct Answer: A
system1:
QUESTION 8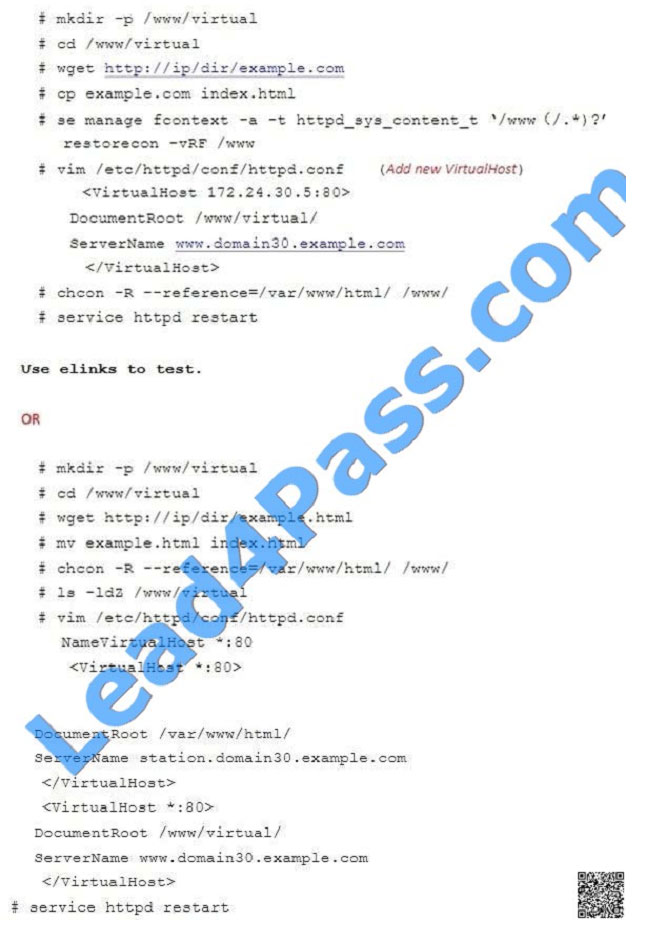
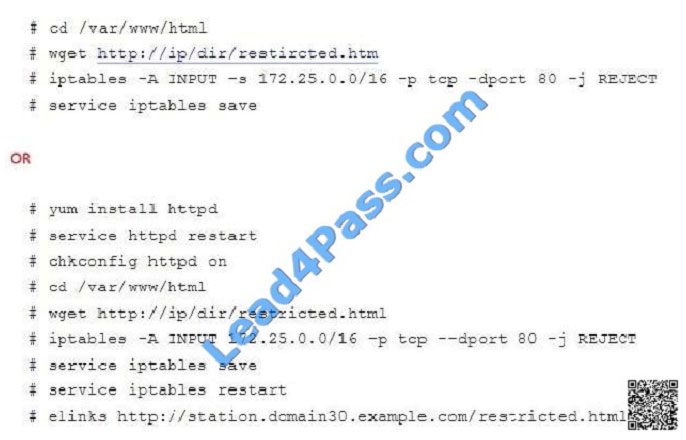
SIMULATION
Download file from http://ip/dir/restircted.html, and the local user harry can access it by
http://station.domain30.example.com/restircted.html, and cannot be accessed by t3gg.com.
A. explanation
Correct Answer: A
QUESTION 9
SIMULATION
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client.
Password for both of the two systems is atenorth
System\\’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the
following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10
The subnet mask is 255.255.255.0
Your system is a member of DNS domain group3.example.com. All systems in DNS domain group3.example.com are
all in subnet 172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless
specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this
domain, this domain provides the following user account:
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in
separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you
made still can be operated after the restart without manual intervention, virtual machine instances of all examinations
must be
able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test using
virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be
found in the following link:
http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the
host and network, although you correctly configured the network service but would have to allow the host or network is
blocked, this also does not score.
You will notice that some requirements which clearly do not allow services be accessed by service domain my133t.org,
systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems of these subnets also belong to my
133t.org
domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform
a series of restrictions on a user, but this user creation may be required in other questions. For convenient
identification,
each exam question has some radio buttons to help you identify which questions you have already completed or not
completed. Certainly, you do not need to care these buttons if you don\\’t need them.
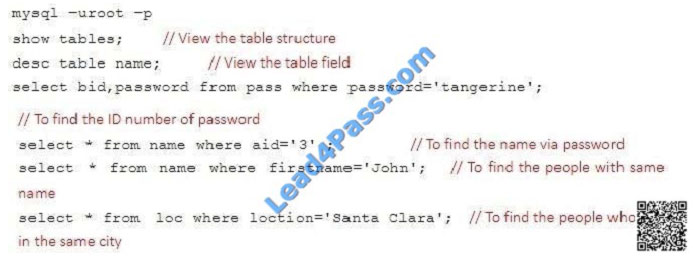
Database Query
Use database Contacts on the system1, and use the corresponding SQL to search and answer the following questions:
1.
What\\’s the person name whose password is solicitous?
2.
How many people\\’s names are John and live is Shanghai at the same time?
A. explanation
Correct Answer: A
QUESTION 10
SIMULATION
RHCE Test Configuration Instructions
Information for the two systems you will use in test is the following:
system1.group3.example.com: is one of the main sever. system2.group3.example.com: mainly used as a client.
Password for both of the two systems is atenorth
System\\’s IP is provided by DHCP, you can regard it as normal, or you can reset to Static IP in accordance with the
following requirements:
system1.group3.example.com: 172.24.3.5
system2.group3.example.com: 172.24.3.10 The subnet mask is 255.255.255.0 Your system is a member of DNS
domain group3.example.com. All systems in DNS domain group3.example.com are all in subnet
172.24.3.0/255.255.255.0, the same all systems in this subnet are also in group3.example.com, unless
specialized, all network services required to be configured can be accessed by systems of domain group3.
host.group3.example.com provides a centralized authentication service domain
GROUP3.EXAMPLE.COM, both system1 and system2 have already been pre-configured to be the client for this
domain, this domain provides the following user account:
Firewall is enabled by default, you can turn it off when deemed appropriate, other settings about firewall may be in
separate requirements.
Your system will be restarted before scoring, so please ensure that all modifications and service configurations you
made still can be operated after the restart without manual intervention, virtual machine instances of all examinations
must be able to enter the correct multi-user level after restart without manual assistance, it will be scored zero if the test
using virtual machine system cannot be restarted or be properly restarted.
Corresponding distribution packages for the testing using operating system Red Hat Enterprise Linux version can be
found in the following link: http://server1.group3.example.com/rhel
Part of the requirements include host security, ensure your host security limit does not prevent the request to allow the
host and network, although you correctly configured the network service but would have to allow the host or network is
blocked, this also does not score. You will notice that some requirements which clearly do not allow services be
accessed by service domain my133t.org, systems of this domain are in subnet 172.25.1.0/252.255.255.0, and systems
of these subnets also belong to my 133t.org domain.
PS: Notice that some test questions may depend on other exam questions, for example, you might be asked to perform
a series of restrictions on a user, but this user creation may be required in other questions. For convenient identification,
each exam question has some radio buttons to help you identify which questions you have already completed or not
completed. Certainly, you do not need to care these buttons if you don\\’t need them.
Configure IPV6 Address
Configure interface eth0 on your test system, using the following IPV6 addresses: 1) The address of system1 should be
2003:ac18::305/64
(2)
The address of system2 should be 2003:ac18::30a/64
(3)
Both two systems must be able to communicate with systems in network 2003:ac18/64 (4) The address must still take
effect after restart
(5)
Both two systems must maintain the current Ipv4 address and can communicate
A.
explanation
Correct Answer: A

QUESTION 11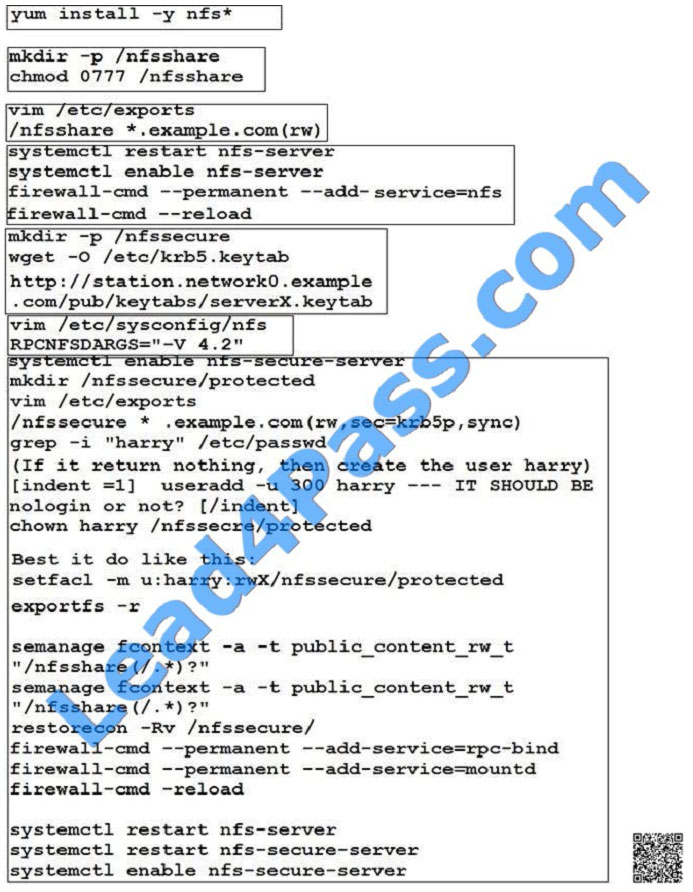
SIMULATION
There were two systems:
system1, main system on which most of the configuration take place
system2, some configuration here
Configure NFS mount.
Mount /nfsshare directory on desktopX under /public directory persistently at system boot time.
Mount /nfssecure/protected with krb5p secured share on desktopX beneath /secure/protected provided with keytab
http://station.network0.example.com/pub/
keytabs/desktopX.keytab
The user harry is able to write files on /secure directory
A. explanation
Correct Answer: A
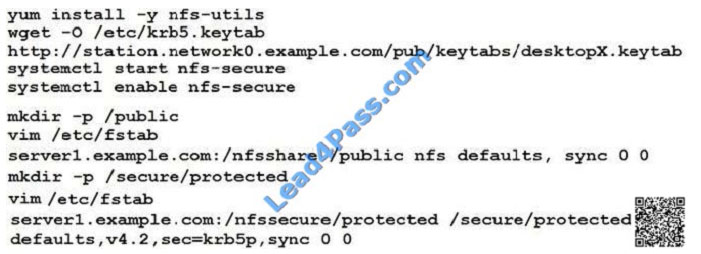
Verification from DesktopX:

QUESTION 12
SIMULATION
Configure the web server, which can be accessed by http://station.domain30.example.com.
A. explanation
Correct Answer: A
QUESTION 13
SIMULATION
One Logical Volume is created named as myvol under vo volume group and is mounted. The Initial Size of that Logical
Volume is 400MB. Make successfully that the size of Logical Volume 200MB without losing any data. The size of logical
volume 200MB to 210MB will be acceptable.
A. explanation
Correct Answer: A
Related EX300 Popular Exam resources
Lead4Pass Year-round Discount Code
What are the advantages of Lead4pass?
Lead4pass employs the most authoritative exam specialists from RedHat, Microsoft, CompTIA, IBM, EMC, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader! Choose Lead4Pass to pass the exam with ease!
Summarize:
It’s not easy to pass the RedHat EX300 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. Lead4pass.com provides you with the most relevant learning materials that you can use to help you prepare.