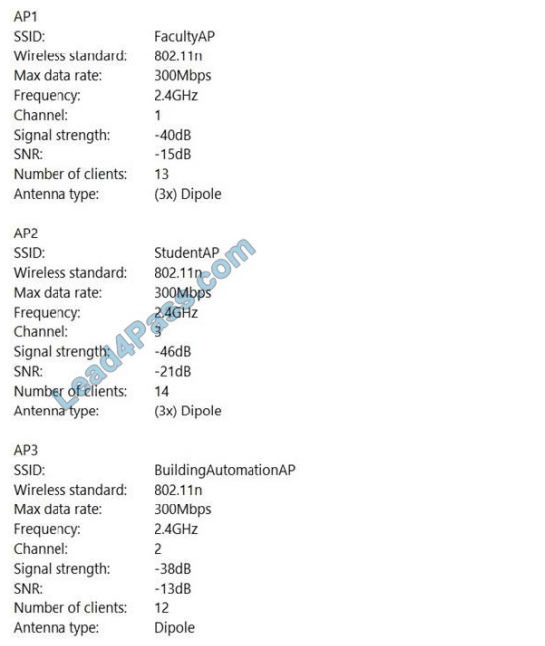
Lead4Pass shares the latest updates and CompTIA xk0-004 test questions and answers! CompTIA xk0-004 dumps authentication problem to ensure real and effective!
Welcome to download the latest Lead4Pass CompTIA xk0-004 dumps with PDF and VCE: https://www.leads4pass.com/xk0-004.html (xk0-004 dumps)
[Latest Updated] CompTIA xk0-004 PDF online download provided by the latest update of Lead4pass
Latest update CompTIA xk0-004 exam questions and answers online practice test
QUESTION 1
A junior systems administrator is scanning archive.tar files with an antivirus scanner. The administrator is given the
following tasks:
1.
List all files that are in the archive.tar files.
2.
Extract all files from the archive.tar files.
Which of the following actions should be performed to meet these requirements? (Choose two.)
A. tar -tvf archive.tar
B. tar -xf archive.tar
C. tar -A archive.tar
D. tar -av archive.tar
E. tar -r archive.tar
F. tar -uvz archive.tar
Correct Answer: AB
Reference: https://linuxize.com/post/how-to-create-and-extract-archives-using-the-tar-command-in-linux/
Exam B
QUESTION 2
Which of the following commands will let a Linux user know the PCI devices that are installed in the system?
A. cat /proc/devices/pci
B. lspci
C. lsdev
D. cat /proc/sys/dev
Correct Answer: B
Reference: https://opensource.com/article/19/9/linux-commands-hardware-information
QUESTION 3
A Linux storage administrator wants to create a logical volume group. Which of the following commands is required to
start the process?
A. pvcreate
B. vgcreate
C. lvcreate
D. mkfs.xfs
Correct Answer: B
Reference: https://www.thegeekstuff.com/2010/08/how-to-create-lvm/
QUESTION 4
A Linux administrator needs to remove a USB drive from a system. The unmount command fails, stating the device is
busy. Which of the following commands will show the reason for this error?
A. lsusb | grep /mnt/usb
B. mount | grep /mnt/usb
C. ps aux | grep /mnt/usb
D. lsof | grep /mnt/usb
Correct Answer: D
Reference: https://www.systutorials.com/force-linux-unmount-filesystem-reporting-device-busy/
QUESTION 5
A Linux administrator is using a public cloud provider to host servers for a company\\’s website. Using the provider\\’s
tools, the administrator wrote a JSON file to define how to deploy the servers. Which of the following techniques did the
administrator use?
A. Infrastructure as code
B. Build automation
C. Platform as a service
D. Automated configuration
Correct Answer: B
Reference: https://cloud.google.com/cloud-build/docs/build-config
QUESTION 6
An administrator receives the following message on a remote server: Cannot open display. Which of the following
should the administrator have used to log in to the server?
A. xrdp -h server.company.com
B. ssh -X server.company.com
C. xvnc server.company.com
D. rdesktop server.company.com
Correct Answer: B
QUESTION 7
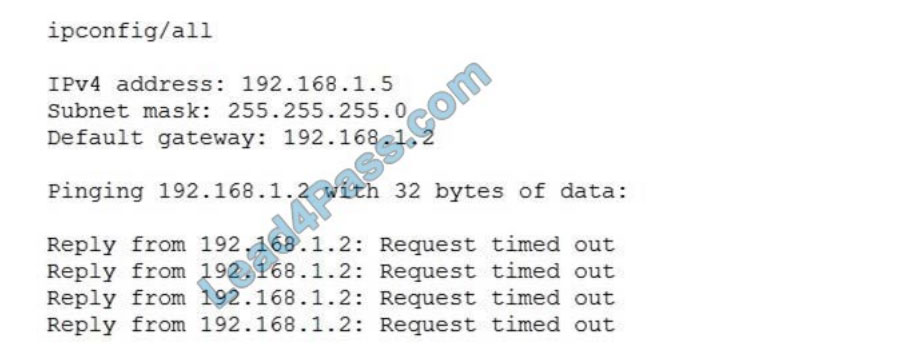
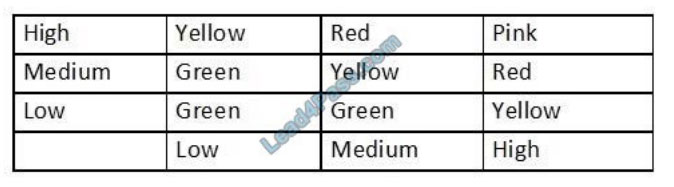
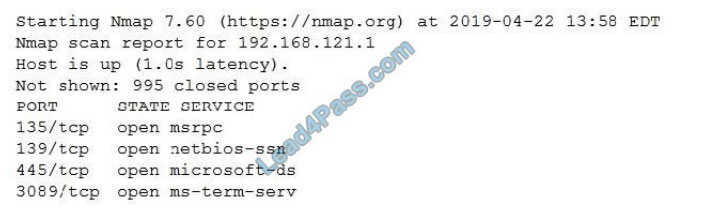
All users are reporting that they cannot connect to the SFTP server. The administrator runs a scan: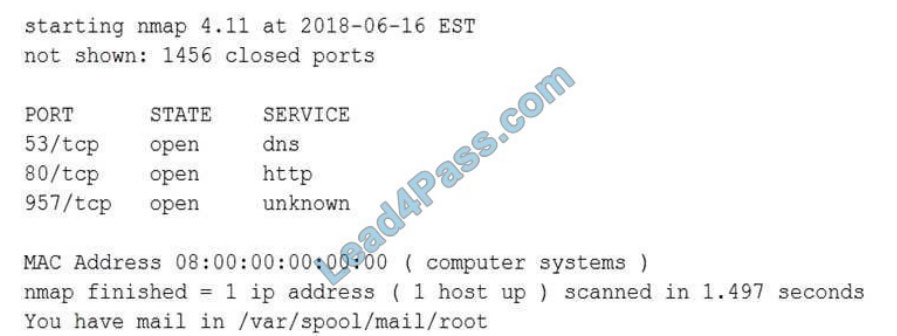
Which of the following would allow the administrator to fix the problem?
A. Allow SFTP connections on port 22 using /etc/sysconfig/iptables.
B. Allow SFTP connections on port 20 and 21 using /etc/sysconfig/iptables.
C. Allow SFTP connections on port 25 using /etc/sysconfig/iptables.
D. Allow SFTP connections on port 1456 using /etc/sysconfig/iptables.
Correct Answer: A
QUESTION 8
A Linux systems administrator needs to set permissions on an application with the following parameters:
The owner of the application should be able to read, write, and execute the application. Members of the group should be
able to read and execute the application. Everyone else should not have access to the application. Which of the
following commands would BEST accomplish these tasks?
A. chmod 710
B. chmod 730
C. chmod 750
D. chmod 760
Correct Answer: D
QUESTION 9
An administrator is logged into a server remotely and wants to determine if the system is a VM. Which of the following
commands would assist with this?
A. dmesg
B. ps
C. top
D. vmstat
Correct Answer: D
Reference: https://ostechnix.com/check-linux-system-physical-virtual-machine/
QUESTION 10
A Linux administrator wants to configure log messages of critical or higher severity levels from the cron utility to be
logged to the console. Which of the following will accomplish this objective?
A. Edit the /etc/logrotate.d/cron file to include the line cron.emerg.* /dev/console
B. Edit the /etc/rsyslog.conf file to include the line cron.emerg.* /dev/console
C. Edit the /etc/logrotate.conf file to include the line cron.emerg.* /dev/console
D. Edit the /etc/rsyslog.d/conf file to include the line cron.emerg.* /dev/console
Correct Answer: B
QUESTION 11
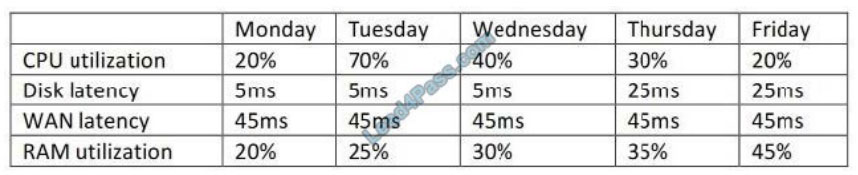
A Linux administrator must identify a user with high disk usage. The administrator runs the # du ? /home/* command
and gets the following output:
Based on the output, User3 has the largest amount of disk space used. To clean up the file space, the administrator
needs to find out more information about the specific files that are using the most disk space. Which of the following
commands will accomplish this task?
A. df –k /home/User/files.txt
B. du –a /home/User3/*
C. du –sh /home/User/
D. find . –name /home/User3 -print
Correct Answer: C
Reference: https://unix.stackexchange.com/questions/37221/finding-files-that-use-the-most-disk-space
QUESTION 12
A configuration management tool running every minute is enforcing the service HTTPd to be started.
To perform maintenance, which of the following series of commands can be used to prevent the service from being
started?
A. systemctl stop httpd andand systemctl mask httpd
B. systemctl disable httpd andand systemctl mask httpd
C. systemctl stop httpd andand systemctl hide httpd
D. systemctl disable httpd andand systemctl hide httpd
Correct Answer: A
QUESTION 13
A junior systems administrator has generated a PKI certificate for SSH sessions. The administrator would like to
configure authentication without passwords to remote systems. Which of the following should the administrator
perform?
A. Add the content of id_rsa.pub file to the remote system ~/.ssh/authorized_keys location.
B. Add the content of id_rsa file to the remote system ~/.ssh/authorized_keys location.
C. Add the content of id_rsa file to the remote system ~/.ssh/known_hosts location.
D. Add the content of id_rsa.pub file to the remote system ~/.ssh/known_hosts location.
Correct Answer: A
Reference: https://kb.iu.edu/d/aews
QUESTION 14
A junior Linux administrator is performing version control on a Git repository. The administrator is given a list of
tasks to complete:
List the currently installed Git release.
Show the status reporting of the clone.
Which of the following commands would allow the administrator to complete these tasks? (Choose two.)
A. git clone –progress
B. git clone –recursive
C. git –help
D. git clone –dissociate
E. git –version
F. git clone –shared
Correct Answer: AC
QUESTION 15
A Linux administrator wants to obtain a list of files and subdirectories in the /etc directory that contain the word
“services”. Once the files and subdirectories are discovered, they should be listed alphabetically in the
/var/tmp/foundservices file. Which of the following shell scripts will accomplish this task?
A. #/bin/bashfind /etc –name services | sort > /var/tmp/foundservices
B. #/bin/bashlocate /etc –sort –name services > /var/tmp/foundservices
C. #/bin/bashfind –name services –sort /var/tmp/foundservices
Correct Answer: B
Lead4pass Update the latest valid CompTIA xk0-004 test questions and answers throughout the year.
The newly uploaded xk0-004 exam practice questions and xk0-004 PDF. Get the complete xk0-004 exam dumps, the latest updated exam questions and answers come from Lead4Pass! Information about Lead4pass xk0-004 Dumps (including PDF and software),
Please dumps lead4pass xk0-004: https://www.leads4pass.com/xk0-004.html (268 Q&A)
Get free CompTIA xk0-004 dumps PDF online